Education
Resource Library
A security program is only as strong as its weakest link. SBS strongly believes in the power of education and security awareness training when it comes to a strong information security program.

Build Your Cybersecurity Culture
Get Free Resources
Share these cybersecurity training tools with your employees and customers to nurture a strong cybersecurity culture at your organization.
-
All
-
eBook
-
Poster
-
Tip Sheet
-
Infographic
-
Other

eBook
Fraudacity Files
eBookFraudacity FilesRead More

eBook
The State of Cybersecurity in Credit Unions
eBookThe State of Cybersecurity in Credit UnionsRead More

Poster
The Golden Rule of Email
PosterThe Golden Rule of EmailDownload
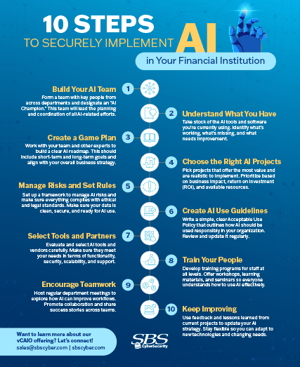
Tip Sheet
10 Steps to Securely Implement AI in Your Financial Institution
Tip Sheet10 Steps to Securely Implement AI in Your Financial InstitutionRead More

eBook
Essential Cybersecurity Best Practices
eBookEssential Cybersecurity Best PracticesDownload

eBook
5 Common Cybersecurity Mistakes Financial Institutions Overlook
eBook5 Common Cybersecurity Mistakes Financial Institutions OverlookRead More

eBook
CEO's Cybersecurity Glossary
eBookCEO's Cybersecurity GlossaryRead More

eBook
Security Awareness Toolkit
eBookSecurity Awareness ToolkitDownload

eBook
Eight Emergency Preparedness Testing Scenarios
eBookEight Emergency Preparedness Testing ScenariosDownload

eBook
Incident Response Preparedness: 50+ Checklist Items
eBookIncident Response Preparedness: 50+ Checklist ItemsDownload

eBook
You Are a Technology Company
eBookYou Are a Technology CompanyDownload

eBook
FDIC InTREx: What Documentation Are You Expected to Have?
eBookFDIC InTREx: What Documentation Are You Expected to Have?Download

eBook
Cybersecurity Tips
eBookCybersecurity TipsDownload

eBook
Defense in Depth Checklist Controls
eBookDefense in Depth Checklist ControlsDownload

eBook
34 Unique Ideas to Create a Culture of Cybersecurity
eBook34 Unique Ideas to Create a Culture of CybersecurityDownload

eBook
5 Key Questions to Consider When Researching a vCISO
eBook5 Key Questions to Consider When Researching a vCISODownload

Infographic
The Three Ws of Investigating Phishing Emails
InfographicThe Three Ws of Investigating Phishing EmailsDownload

Infographic
Don't Take the Bait
InfographicDon't Take the BaitDownload

Tip Sheet
Microsoft Office 365 Security Suggestions
Tip SheetMicrosoft Office 365 Security SuggestionsDownload

Tip Sheet
Investigating Phishing Emails
Tip SheetInvestigating Phishing EmailsDownload

Tip Sheet
Password Tips
Tip SheetPassword TipsDownload

Poster
Don't Get Hooked
PosterDon't Get HookedDownload

Infographic
Information Technology vs. Information Security
InfographicInformation Technology vs. Information SecurityDownload
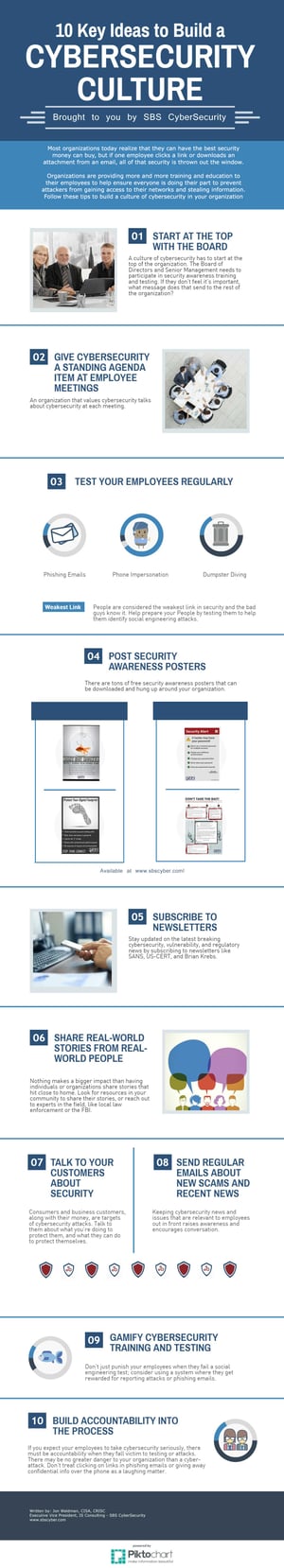
Infographic
10 Key Ideas to Build a Cybersecurity Culture
Infographic10 Key Ideas to Build a Cybersecurity CultureDownload

Infographic
The SBS Risk Management Method
InfographicThe SBS Risk Management MethodDownload

Other
Sounds of Cybersecurity
OtherSounds of CybersecurityListen

Other
Cybersecurity Heroes Coloring Pages
OtherCybersecurity Heroes Coloring PagesRead More
Webinars
February 26, 2026
Hacker Hour: Understanding Stablecoins
Explore stablecoins, their rise in finance, regulatory considerations, and how they could transform payments, settlement, and liquidity.
Watch Webinar
January 28, 2026
Hacker Hour: Creative Ideas to Spark a Cyber-Aware Culture
Explore creative, practical ideas to spark a more engaged cyber-aware culture across your organization.
Watch Webinar
December 09, 2025
Hacker Hour: Examination Readiness — A Roadmap to Success
Uncover best practices for exam readiness, insights from real-world experience, and the top regulatory focus areas for 2026.
Watch Webinar
February 12, 2026
Cyber Showcase: Revisiting CRI — A Guide for Procrastinators
Revisit the CRI Profile—its purpose, alignment with other risk frameworks, and whether it truly fits as your long-term replacement.
Watch Webinar
January 28, 2026
Cyber Showcase: Who's in Charge of AI? Introducing the vCAIO
Discover why institutions are losing control of AI, what regulators are expecting, and how a vCAIO can help your organization adopt AI confidently.
Watch Webinar
December 09, 2025
Cyber Showcase: 2026 TRAC State of the State
Celebrate TRAC’s milestone year and explore what’s next for 2026. Discover strategies to strengthen your organization’s risk management and compliance.
Watch Webinar

Get Certified
Looking to enhance your cyber education with a focus on the banking industry? Look no further than the SBS Institute! Choose a course tailored to your specific role for a flexible and targeted learning experience.
Blog Posts
Nick PodhradskyFebruary 26, 2026
Hacker Hour: Understanding Stablecoins
Explore stablecoins, their rise in finance, regulatory considerations, and how they could transform payments, settlement, and liquidity.
Start Reading
SBS CyberSecurityFebruary 24, 2026
Why Fraud Awareness Still Matters for Banks and Credit Unions
Financial scams rely on urgency and emotion. Learn why fraud education still matters and download a guide for banks and credits unions to share with customers.
Start Reading
SBS CyberSecurityFebruary 13, 2026
SBS Institute Webinar: 2026 Audit Survival Guide—Top 10 Recommendations
Use this audit survival guide to navigate critical findings for 2026, strengthen compliance, reduce vulnerabilities, and stay ahead of emerging threats.
Start Reading
What would you like to do next?
Hear From Our Clients
See what companies like yours are saying about partnering with SBS!
Read Testimonials
View All Blogs
Get resources that simplify complex concepts, offer practical tips, and keep you informed.
Go to the Blog
![Icons_HackerHour]() Free Hacker Hour Webinar Series
Join us for this interactive and engaging cybersecurity training experience.
See Hacker Hours
Get Certified
Join the growing community of professionals committed to strong cybersecurity and career advancement with an SBS Institute certification.
Get the Details
Start My Journey
Book a meeting with one of our experts to learn more about partnering with SBS.
Book a Meeting
Free Hacker Hour Webinar Series
Join us for this interactive and engaging cybersecurity training experience.
See Hacker Hours
Get Certified
Join the growing community of professionals committed to strong cybersecurity and career advancement with an SBS Institute certification.
Get the Details
Start My Journey
Book a meeting with one of our experts to learn more about partnering with SBS.
Book a Meeting
![Icons_TRAC]() Simplify Compliance
Learn how TRAC takes the guesswork out of cybersecurity risk management and compliance.
Get the Details
Simplify Compliance
Learn how TRAC takes the guesswork out of cybersecurity risk management and compliance.
Get the Details

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)