NIST CSF
From initial implementation to full integration, TRAC's user-friendly NIST CSF module offers detailed guidance, practical examples, and expert insights to ensure you meet the highest standards of cybersecurity. Whether you're just starting out with the NIST Cybersecurity Framework or looking to refine your existing practices or improve your security posture with actionable reports, our NIST CSF module is there for you every step of the way.

Comprehensive Guided Approach
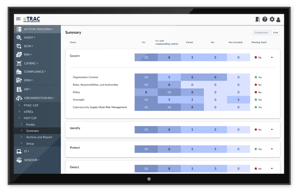
Are you ready to implement the NIST Cybersecurity Framework in your organization? With practical implementation examples and precise references for each statement, TRAC's NIST CSF module empowers you to confidently answer all the questions posed by the NIST Cybersecurity Framework. Document your reasoning, track goals for each statement and domain, assign tasks to improve your posture, and effortlessly report on your data.
Start Now, It's Easy
Begin integrating the NIST Cybersecurity Framework 2.0 within your organization. Get a demo of our premium software, or get started with free tools.
Minimal Workload, Maximum Results
NIST CSF Module Features
Choosing the Right Cybersecurity Framework with TRAC
Which One Is Right for You?
The TRAC Ecosystem
TRAC adapts to your business needs with its suite of modules that can work independently or tightly manage your risk with intermodular operability.Read More

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)