Executive Summary
Marquis Software Solutions, a widely used data analytics and marketing provider for banks and credit unions, confirmed a ransomware attack that exposed sensitive customer information across more than 70 financial institutions. Attackers gained access through a SonicWall firewall vulnerability, exfiltrated data from Marquis’s systems, and triggered a wave of state-level breach notifications and regulatory expectations.
For financial institutions, the incident is a pointed reminder: Even trusted service providers can be single points of failure. This is as much about vendor risk and resilience as it is about cybersecurity controls.
What Happened in the Marquis Data Breach
On August 14, 2025, Marquis Software Solutions experienced a ransomware attack after threat actors breached its network through a SonicWall firewall. Although the attack occurred in mid-August, Marquis only recently began issuing regulatory notifications and individual breach notices, bringing the full scope of the event to light.
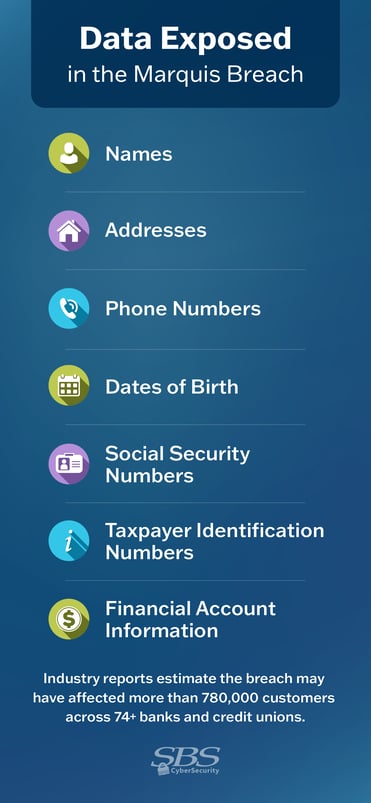
During the intrusion, attackers exfiltrated files containing customer data provided to Marquis by its client institutions. The information involved included names, addresses, phone numbers, dates of birth, Social Security numbers, Taxpayer Identification Numbers, and certain financial account information. Current state breach filings account for more than 400,000 affected consumers across at least 74 banks and credit unions, though aggregated industry reporting estimates the total may surpass 780,000 individuals nationwide.
Marquis has stated that there is currently no evidence of data misuse and is offering complimentary credit monitoring and identity protection services to affected individuals. Reports that a ransom was paid to prevent publication of the stolen data have circulated but remain unconfirmed by Marquis.
For institutions relying on Marquis, this quickly turned into an operational and regulatory challenge — often before they had full clarity on their own exposure.
Why It Mattered
This incident underscored three realities for financial institutions:
Vendor Reliance Amplifies Risk
Many organizations depend on Marquis for data management, CRM workflows, and compliance reporting. When a provider with this level of access experiences a breach, institutions inherit the downstream impact.
Data Exposure Extends Beyond What Many Realize
Several impacted organizations did not initially know what types of data Marquis held on their behalf. That gap complicates reporting, customer notification timelines, and examiner expectations.
Resilience Must Include Third Parties
Strong internal controls do not offset the risk introduced by critical providers. Vendors are part of the institution’s operational footprint, and regulators now routinely expect evidence of vendor oversight in examinations and breach responses.
Key Lessons
Map Your Data — Including What Vendors Hold
Institutions must maintain clarity on what data each vendor collects, processes, and stores. Incomplete visibility leads to uncertainty, delays, and regulatory strain when a breach occurs.
Review Third-Party Security Controls Beyond the Checklist
Annual questionnaires alone do not confirm whether firewalls are patched, VPN accounts are secured, or unused credentials have been removed. Oversight must include deeper control validation, especially for high-access providers.
Operational Dependencies Matter as Much as Technical Ones
Marquis’s role in CRM workflows, marketing campaigns, and compliance reporting meant the impact extended beyond data exposure. Understanding how vendor compromise affects daily operations is essential for business continuity planning.
Initial Access Tactics Continue to Evolve
The breach leveraged a SonicWall vulnerability that had a public patch available, underscoring the need for rapid patching, multifactor authentication (MFA) enforcement, and credential hygiene across remote access systems.
Practical Next Steps
1. Confirm Your Exposure
Identify exactly what data was sent to Marquis and whether it aligns with state breach notification filings.
2. Evaluate Notification and Reporting Obligations
Work with legal and compliance teams to determine customer notification requirements, regulator reporting timelines, and board disclosure thresholds.
3. Reassess Vendor Risk Tiering
Elevate vendors handling critical data or compliance support to higher risk tiers with corresponding oversight.
4. Validate Controls for All Remote Access Systems
Ensure all firewall and VPN access points — internal and third-party — are fully patched, MFA-protected, and free of unused or legacy accounts.
5. Strengthen Resilience Planning for Critical Vendors
Incorporate third-party compromise scenarios into tabletop exercises and continuity plans to ensure your institution can maintain essential functions if a critical vendor is disrupted.
6. Review Contracts and Insurance Triggers
Examine your contracts for data breach notification clauses, data location terms, and cyber insurance triggers to confirm coverage and obligations.
7. Enhance Monitoring for Downstream Fraud
Given the data types exposed, step up monitoring for both accounts and transactions to detect unusual activity tied to SSNs, DOBs, and account numbers.
Don’t Wait Until It’s Too Late
The Marquis breach demonstrates that even well-established vendors can introduce significant risk. The goal isn’t to eliminate all risk — that’s impossible — but to understand exposure, strengthen oversight, and maintain continuity when incidents occur.
Institutions that proactively map data held by third parties, validate vendor controls, and test vendor-breach scenarios will be better positioned to respond quickly and confidently. Preparedness today reduces uncertainty tomorrow, helping to safeguard operations and maintain customer trust when the unexpected arises.
![]()
Turn Lessons Into Action

Incident response plans are not one-size-fits-all. Get a customized plan that aligns with your industry regulations, business objectives, and specific security needs.
Read More
As your organization grows and incorporates more vendor relationships, the need for a strong vendor management program also grows.
Read More

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
