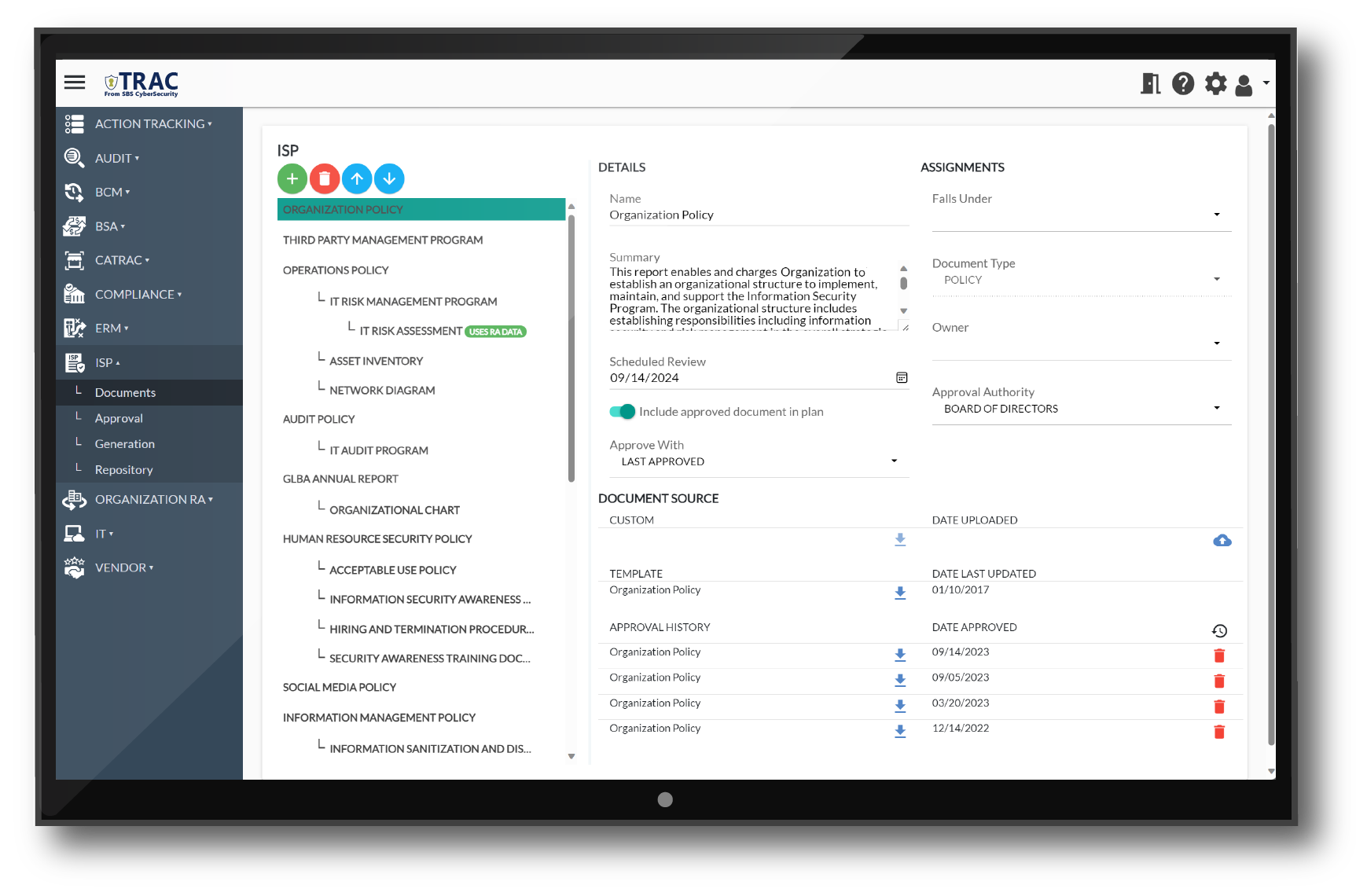
Information Security Program
Avoid the frustration of developing and maintaining a comprehensive information security program by using TRAC’s built-in templates, ensuring your documents are all up-to-date and approved – making it a living document.

Seamless Program Maintenance
Don’t Reinvent the Wheel
Having good policies and procedures is not just critical from a regulatory perspective but also to help ensure you are equipped to handle the ever-changing world of cybersecurity. Use TRAC’s template library to create an Information Security Program in hours instead of days or even weeks.
Add Your Own
Confident in your information security program documentation? Feel free to upload them into TRAC so your ISP can be a living, breathing document instead of sitting in a three-ring binder on a shelf collecting dust.
See how TRAC can work for you!
Let us show you how TRAC powers businesses like yours with a product demo.
Minimized Workload, Maximized Results
Add a (Virtual) Security Expert
The built-in intelligence in TRAC is the result of more than 1,100 hours of research completed annually by SBS experts, giving you virtual access to a seasoned security expert at a fraction of the cost of hiring one.
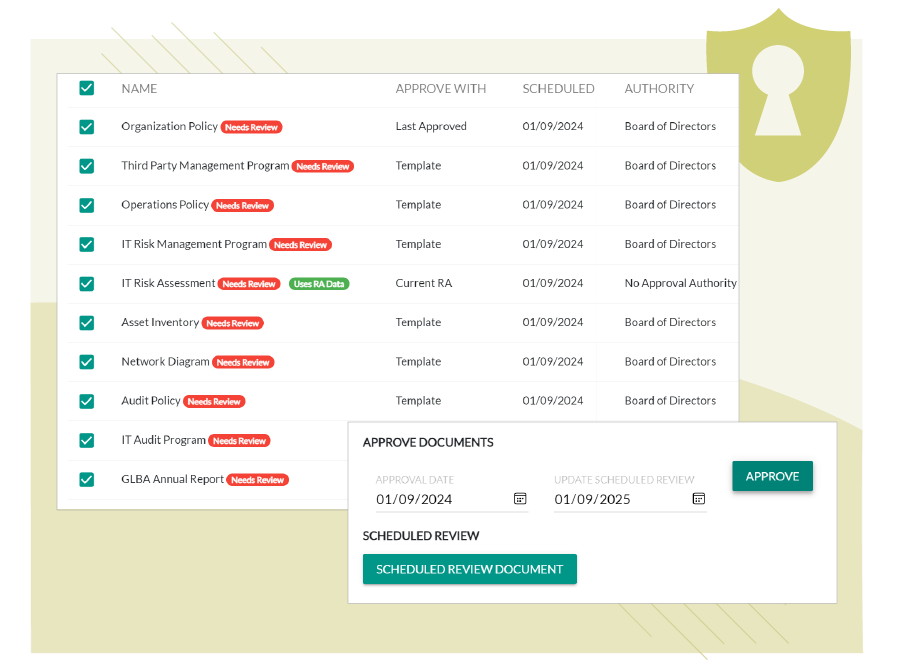
Don’t Stress About Regulatory Updates
SBS experts work tirelessly to make sure our template library is updated as often as necessary, be it changes to existing documents or the addition of new ones.
Avoid the Blob
A good information security program is updated as needed and carefully curated – that is to say, don’t just add stuff to your ISP for the sake of adding or tracking documents without removing unnecessary ones. TRAC can help you avoid the “blob” to ensure your program contains the documents that are needed and only the documents that are needed.
Powerful Access Controls
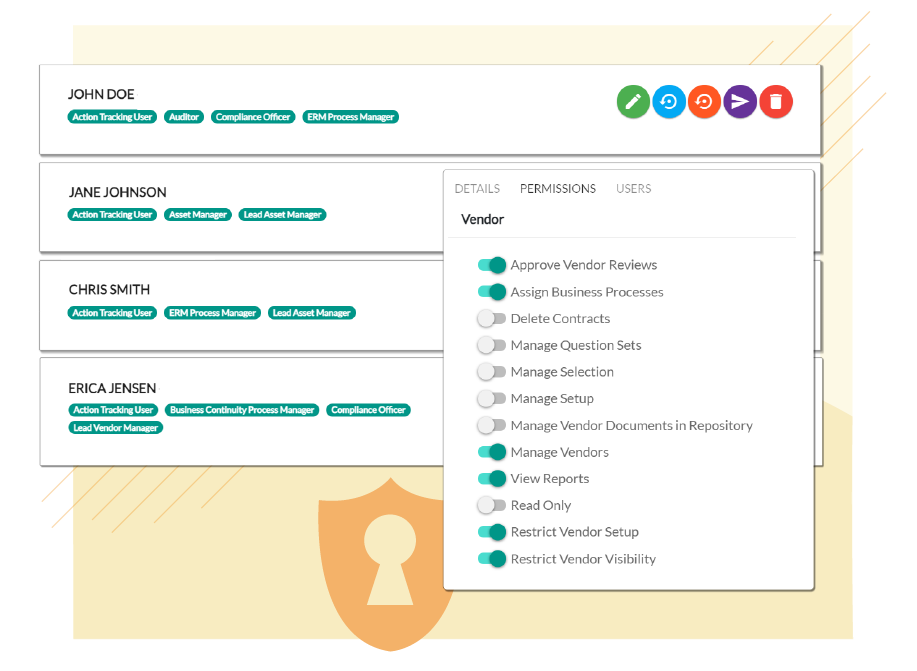
Unlimited Users
A good cybersecurity culture means not having it fall all on one person’s shoulders. TRAC allows you to pull as many people into the process as necessary, acting as the hub for collaboration to complete information security tasks without any hidden fees for additional users.
User-Specific Access
Easily customize roles and responsibilities to ensure each user has access to what they need, but not more than they should.
Action Logging
TRAC’s searchable activity logs provide extensive detail on all actions performed on the platform, helping you understand who did what and when.
Unrivaled Support

Get TRAC Help When You Need It
Have a TRAC question or just need additional training? Dedicated support staff are available now or in the future at no extra cost. More of a “self-help” type? Access user guides, reference sheets, and other educational materials at the click of a button.
Join Our User Group
Attend online TRAC User Group meetings to gain exclusive insights into upcoming enhancements, share best practices, and uncover helpful tips and tricks. Additionally, you'll have the chance to directly connect with our product and development team and contribute your input towards future functionality.
What's Next?
The TRAC Ecosystem
TRAC adapts to your business needs with its suite of modules that can work independently or tightly manage your risk with intermodular operability.Read More

Certified Banking Security Manager
Mature and manage your information security program to meet cybersecurity and regulatory expectations. The resources and exercises available with this course will help you develop valuable material to take back to your institution.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
