Centralized solution for creating and tracking security tasks and plans. Remain diligent with remediation and follow-up.
TRAC: Cybersecurity Risk Management Software
Eliminate the hassle of risk assessments, vendor management, business continuity planning, and other essential cybersecurity tasks with TRAC. Designed to surpass traditional spreadsheets, TRAC simplifies your governance, risk, and compliance with valuable insights to enhance decision-making across your organization.
Benefits of TRAC as Your GRC Tool
Handling complex information security tasks often means facing challenges related to time, manpower, expertise, and patience. While spreadsheets are commonly used, they aren't designed for sophisticated risk management. Enter TRAC — a GRC platform created specifically for this purpose.
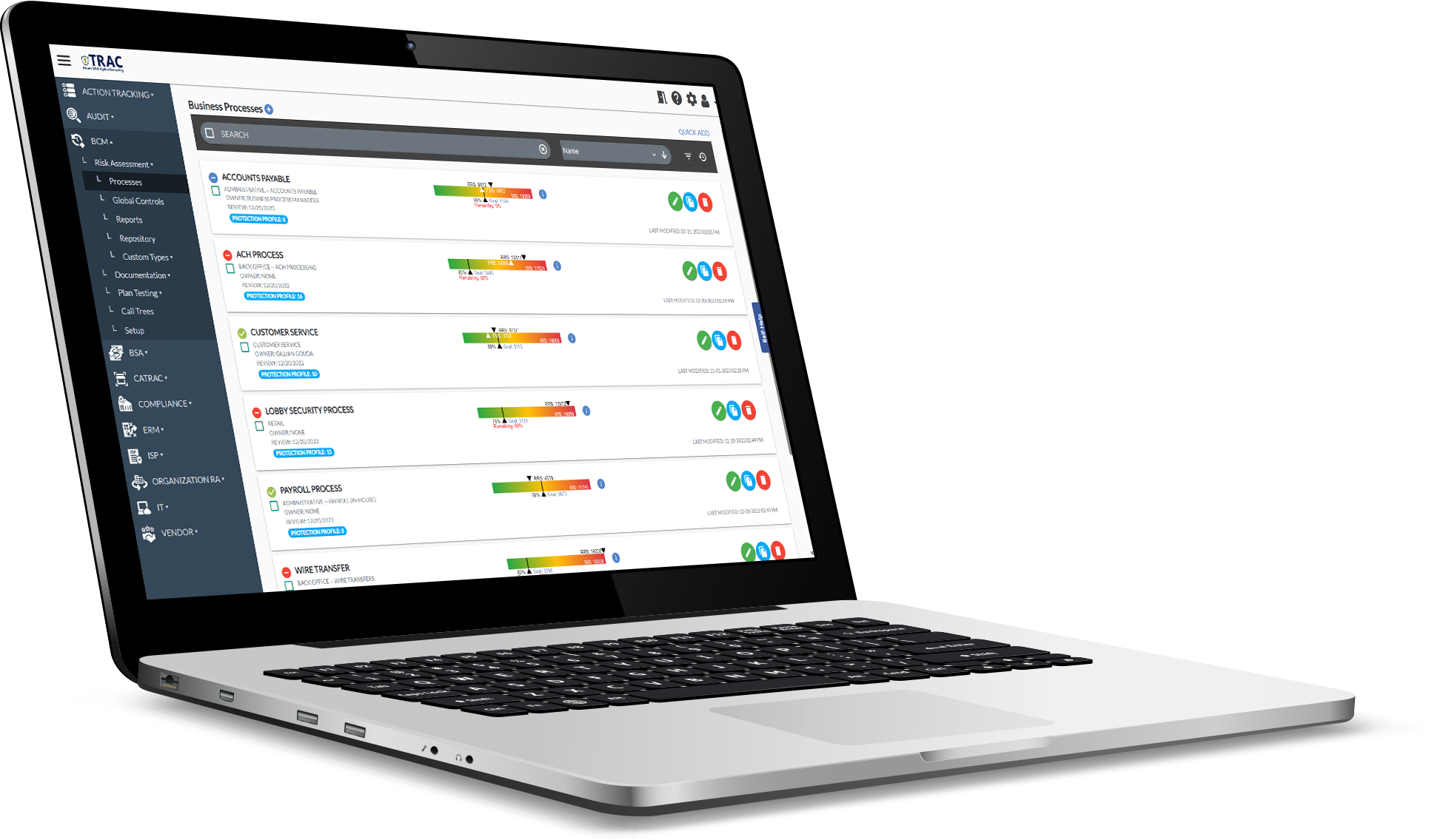
Spreadsheets can't keep up anymore.
When it comes to completing complex information security tasks, organizations often grapple with the same persistent challenges: time, manpower, expertise, and patience. Spreadsheets are the most common approach to performing these duties, but spreadsheets weren’t created for the level of sophisticated risk management – TRAC was.
Backed by a team of cybersecurity experts and filled with easy-to-use workflows and built-in intelligence, using TRAC is the equivalent of adding a cybersecurity expert to your team at a fraction of the cost of hiring one.
- Time-tested and used successfully for thousands of exams and audits.
- Robust assessment model with results you can measure.
- User-friendly interface with full customization options to fit your needs.
- Built-in intelligence and continuous updates to industry-specific profiles, threats, controls, and categories.
- Quickly adjust to regulatory updates and changes to the cyber landscape.
SEE HOW TRAC CAN WORK FOR YOU!
Let us show you how TRAC powers businesses like yours with a product demo.
Governance
Centralize governance activities such as policy management, task management, and executive oversight. TRAC empowers institutions to maintain consistency, transparency, and control over their security posture and action items.

Protect critical systems by managing employee access, detecting risky permissions, and preventing insider threats.
Build and maintain a compliant, up-to-date information security program with guided templates, integrated change management, and ready-to-share documentation.
Risk
Map critical assets, evaluate vulnerabilities, and prioritize risks based on real-world consequences rather than generic checklists. Automated scoring, vendor risk tracking, and continuous monitoring help teams shift from reactive firefighting to proactive planning, ensuring that resources are directed toward the most pressing exposures
Measure and track cybersecurity readiness with the NCUA ACET tool, build your risk profile, and share clear, goal-aligned reports instantly.
Simplify the creation and maintenance of your business continuity plan and processes with automated business impact analysis.

Commercial customers insights, security education, and actionable recommendations through assessments and surveys.
Gain a clear view of your organization’s cybersecurity risk with a financial-grade framework and reports everyone can understand.
Centralize enterprise risk management with intelligent workflows, customizable controls, and real-time regulatory insights.
Strengthen FDIC IT exam readiness with proactive gap detection, automated simulations, and clear, actionable reporting.
Streamline your ISP risk assessment with gap analysis, policy management, and instant board-ready reporting.
Comprehensive and quantifiable asset-based risk assessment with hundreds of industry-specific presets.
Apply the NIST framework to gain a complete view of your security posture, supported by expert guidance and practical tools for top-tier cybersecurity.
Manage all aspects of your vendor relationships effortlessly, and with transparency.
Compliance
Streamline your compliance efforts by automating audits, tracking control effectiveness, improving accuracy, and demonstrating compliance efficiently and confidently.

Exceed BSA compliance standards with centralized risk assessments, full policy coverage, and penalty-preventing insights.
Stay compliant with centralized regulatory insights, streamlined process tracking, and board-ready reports that clearly show your organization’s status.
Conduct and track internal audits with customizable templates, thorough control reviews, and streamlined reporting for effective risk mitigation.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)

