Network Penetration Testing Services

Strengthen Your Cyber Defenses with Network Penetration Testing
A penetration test is a controlled cybersecurity assessment designed to evaluate your organization's ability to withstand cyber threats. Ethical hackers attempt to exploit vulnerabilities in your network, applications, and security infrastructure to identify weaknesses before malicious actors do.
With SBS CyberSecurity, you get expert penetration testing services tailored to your business’s security needs.
- Pinpoint vulnerabilities in your IT infrastructure and prioritize areas for improvement.
- Enhance risk management by identifying security gaps and implementing proactive mitigation strategies.
- Strengthen incident response capabilities to detect and mitigate threats effectively, ensuring business continuity.
Benefits of Network Penetration Testing
At SBS CyberSecurity, we go beyond technical assessments. Our experts provide clear reports and actionable recommendations that empower your organization to enhance security defenses effectively.
START MY JOURNEY!
A penetration test provides a strategic roadmap for identifying and mitigating potential threats, reinforcing your commitment to proactive cybersecurity and effective risk management.
Book a meeting to learn more about partnering with SBS.
Features of Our Penetration Testing Services
Partner with SBS to test your network from the outside to actively discover, exploit, and report any vulnerabilities that may impact the confidentiality, integrity, and availability of your IT systems.
Comprehensive Network Testing Process
Follow Up
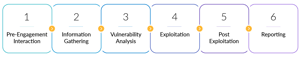
Our Proven Penetration Testing Methodology
Our ethical hackers follow a six-step methodology to ensure thorough security penetration testing.
Hear What Our Clients Say!
⭐⭐⭐⭐⭐ 09/04/2024
"We contracted with SBS for a couple of reasons; we use them for IT/Cyber audits such as Network Security Assessments, IT Controls, Tabletop Testing, annual Training, M365 reviews, and Wireless penetration testing. We also use their TRAC software for all our policies and risk assessements as well as tracking action items from audit findings. Along with the TRAC software we invested in consulting services that continue help keep our program on track and up to the latest requirements."
⭐⭐⭐⭐⭐ 09/04/2024
"If you are looking for a company that has the knowledge and skill of a huge corporation with the service of a local "hometown" business, this is it! I can't say enough about the employees and their willingness to help in any situation. I've been through a certification course as well as utilize SBS for services and I have never been disappointed. In fact, they are probably one of the vendors that I couldn't do without in my position as ISO. The company and the employees are a pleasure to work with."
⭐⭐⭐⭐⭐ 09/30/2024
"If you're looking for a fully managed service to support your vendor reviews, SBS CyberSecurity fills that gap. The team is responsive and a pleasure to collaborate with, especially with the knowledge and experience they bring to the table. Having them as an extension of the team ensures that we meet regulatory demands and allocate our resources to other critical tasks. Thank you!"
SBS CYBERSECURITY IS AN EXCELLENT CUSTOMER TO WORK WITH!!
Heather B.
⭐⭐⭐⭐⭐ 10/26/2023
"Everyone that we have worked with at SBS CyberSecurity is very knowledgeable about the topics they are helping us with. They are more than willing to provide you data to help in any decision-making situations."
SBS CYBERSECURITY IS A TRUSTED PARTNER FOR US!
Shauna E. | Small-Business
⭐⭐⭐⭐⭐ 11/08/2023
"Everyone at SBS CyberSecurity has the necessary industry knowledge to support our credit union and its needs. Their customer support is top-notch. They are always available and follow through with what they say they will do. The various modules that SBS offers relate to our business needs."
SBS PROVIDES SUPERIOR IT AUDITS AND TESTING
Jeff V. | Small-Business
⭐⭐⭐⭐⭐ 11/28/2023
"The depth of testing they provide is like nothing I've seen from other vendors. We've always done external penetration testing and internal vulnerability scans, but SBS takes it a step further to show security gaps which were not discovered in the past. We've reached out to them long after the audit was completed and they were very helpful with any questions or clarification we had."
SBS CYBERSECURITY PROVIDES AND INVALUABLE SERVICE FOR SMALL BANKS
Kim P. | Banking
⭐⭐⭐⭐⭐ 11/14/2023
"I did not have to re-create the wheel to develop a comprehensive Information Security Program. The TRAC software has all the components, including policies, that are easy to use! I like how the program separates the requirements into different modules, as this is much easier to implement, but the end product integrates these modules and documents it into a comprehensive program that is usable."
FANTASTIC CUSTOMER SERVICE
Verified User in Banking | Small-Business
⭐⭐⭐⭐⭐ 11/09/2023
"I have enjoyed working with our assigned consultant, but I have had the opportunity to work with numerous employees throughout SBS and all of them have been friendly, professional, and offered exceptional customer service. Kudos to SBS for building a strong, exceptional environment for their employees to thrive in."
SECURITY TESTING WITH THE BEST
Jessica R. | Mid-Market
⭐⭐⭐⭐⭐ 11/09/2023
"SBS CyberSecurity performed my security penetration audit on our hospital's network this year. Our consultant provided excellent assistance with gathering information to perform the test as well as providing solutions that we were able to implement. They helped us recognize a flaw where the outside guest wifi could access the internal network which we were quickly able to stop with their assistance while the test was being performed."
REQUEST A QUOTE!
Cyber threats evolve constantly - stay ahead with SBS CyberSecurity’s Penetration Testing Services. Our tailored security assessments help protect your data, ensure compliance, and give you peace of mind.
Don’t wait until a breach happens. Partner with SBS CyberSecurity today.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
