TRAC: Cybersecurity Risk Management Software
Take the frustration out of risk assessments, vendor management, business continuity management, and other critical cybersecurity risk management tasks. Unlike spreadsheets that offer annoying, manual processes without any promise of usable data, TRAC was built to help you easily demonstrate compliance while also giving you the information you need to make the best decisions for your organization.
Spreadsheets can't keep up anymore.
When it comes to completing complex information security tasks, organizations often grapple with the same persistent challenges: time, manpower, expertise, and patience. Spreadsheets are the most common approach to performing these duties, but spreadsheets weren’t created for the level of sophisticated risk management – TRAC was.
Backed by a team of cybersecurity experts and filled with easy-to-use workflows and built-in intelligence, using TRAC is the equivalent of adding a cybersecurity expert to your team at a fraction of the cost of hiring one.
- Time-tested and used successfully for thousands of exams and audits.
- Robust assessment model with results you can measure.
- User-friendly interface with full customization options to fit your needs.
- Built-in intelligence and continuous updates to industry-specific profiles, threats, controls, and categories.
- Quickly adjust to regulatory updates and changes to the cyber landscape.

Spreadsheets can't keep up anymore.
When it comes to completing complex information security tasks, organizations often grapple with the same persistent challenges: time, manpower, expertise, and patience. Spreadsheets are the most common approach to performing these duties, but spreadsheets weren’t created for the level of sophisticated risk management – TRAC was.
Backed by a team of cybersecurity experts and filled with easy-to-use workflows and built-in intelligence, using TRAC is the equivalent of adding a cybersecurity expert to your team at a fraction of the cost of hiring one.
- Time-tested and used successfully for thousands of exams and audits.
- Robust assessment model with results you can measure.
- User-friendly interface with full customization options to fit your needs.
- Built-in intelligence and continuous updates to industry-specific profiles, threats, controls, and categories.
- Quickly adjust to regulatory updates and changes to the cyber landscape.
SEE HOW TRAC CAN WORK FOR YOU!
Let us show you how TRAC powers businesses like yours with a product demo.
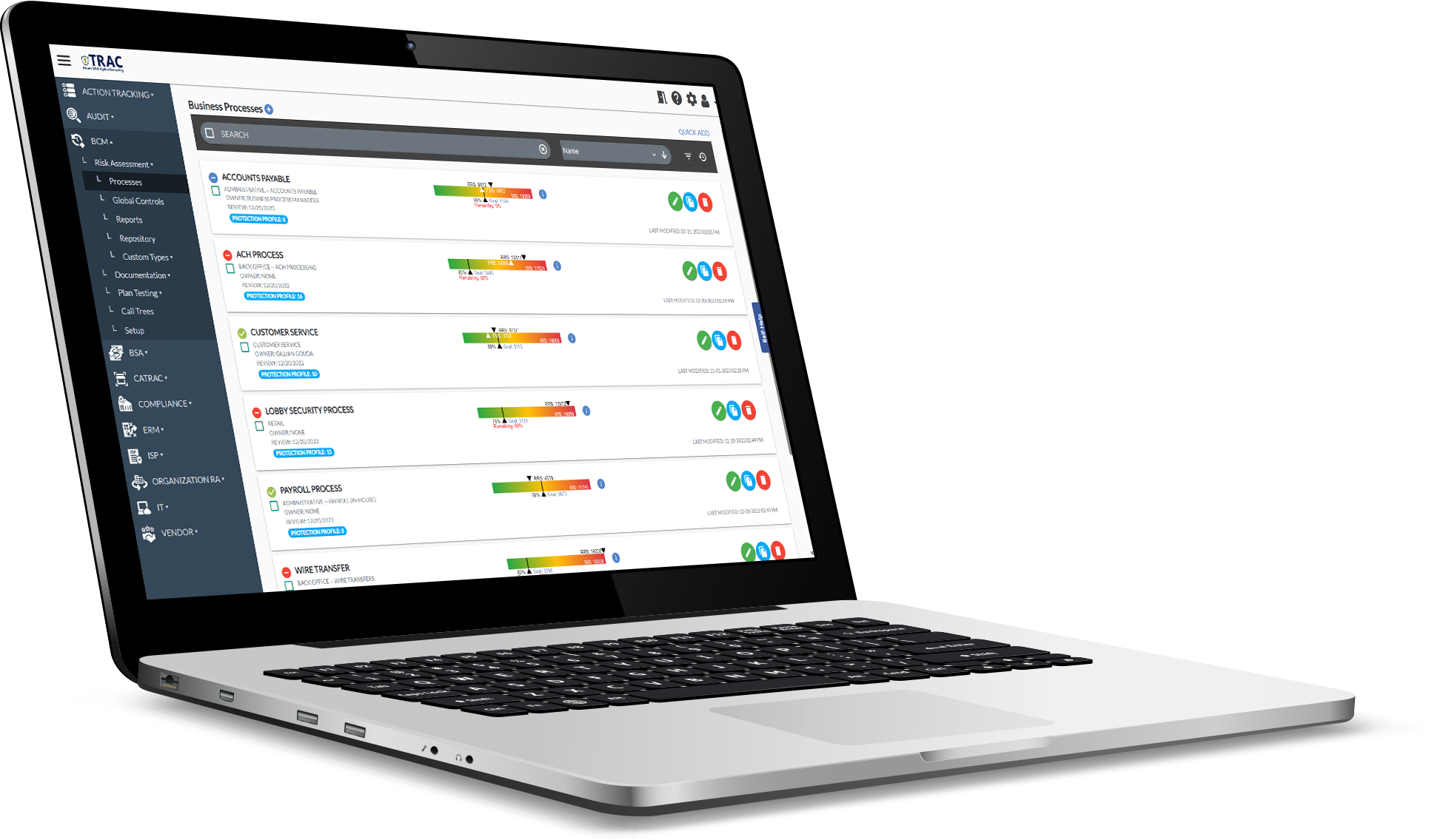
TRAC significantly speeds up the process of executing essential cybersecurity tasks, such as conducting comprehensive risk assessments, which involve identifying, evaluating, and prioritizing potential threats; managing vendor relationships to ensure that third-party partners adhere to strict security standards; and ensuring robust business continuity management, which includes developing strategies and plans to maintain operations during and after a disruption. By streamlining these critical functions, TRAC enhances organizational security posture and operational efficiency.
At the same time, the integrated nature of our modules eliminates duplication of efforts, saving time and resources. This integration ensures that information flows seamlessly between different functions, reducing redundancy and minimizing manual input. Consequently, organizations can allocate their resources more effectively, focusing on strategic initiatives rather than repetitive tasks, thus optimizing resource allocation and enhancing overall productivity.
You are not likely operating with an unlimited budget when it comes to securing your information and cybersecurity infrastructure. Instead, you're tasked with the challenging responsibility of maximizing every dollar allocated to security measures. This means carefully evaluating and strategically deploying resources to ensure that your investments are as effective and efficient as possible, without compromising on the safety and integrity of your systems and data.
TRAC’s advanced built-in intelligence and dynamic reporting features deliver substantial cost savings and empower you with deeper insights. Backed and refined by our in-house cybersecurity experts, these tools enable you to make informed decisions, ensuring that every dollar spent contributes to enhancing your security posture and maximizing the overall return on your investment.
Studies show that a vast majority of executives believe cybersecurity issues hinder expansion, as many businesses face significant challenges in managing digital threats that can disrupt their operations, tarnish their brand image, and result in costly financial penalties. These cybersecurity concerns often lead to hesitancy in investing in new technologies or entering new markets, as executives weigh the risks of potential data breaches against the benefits of growth. Furthermore, the complexity and evolving nature of cyber threats require organizations to allocate substantial resources to develop and implement robust security measures, which can divert attention and funding away from expansion initiatives. As a result, addressing cybersecurity issues has become a critical priority for leaders who aim to ensure sustainable growth and maintain a competitive edge in their respective industries.
TRAC accelerates the work of completing cybersecurity functions like risk assessments, vendor management, and business continuity management.
At the same time, the integrated nature of our modules eliminates duplication of efforts, saving time and resources.
Chances are good that you don’t have a blank check when it comes to information and cybersecurity; you have to make the most of every security dollar.
TRAC’s built-in intelligence and dynamic reporting provide significant cost savings and help you better understand how to get the most bang for your buck.
Studies show that a vast majority of executives believe cybersecurity issues hinder expansion.
TRAC users can remove obstacles to growth and help prevent significant losses due to fines, legal hassles, breaches, and reputational damage.
TRAC Core Modules

Vendor
No one likes doing Vendor Management, but it is critically important. Use TRAC to develop the guidelines for your vendor management program, undergo a thorough selection process to ensure you find the right partner, and easily conduct ongoing monitoring of your current third-party relationships.
IT
Quickly conduct an IT risk assessment to gain valuable insights into the risks posed by your assets, the controls you currently have in place to mitigate those risks, and identify areas where additional resources can be utilized to better protect your organization in the future.
Business Continuity Management (BCM)
How would you get your organization back up and running if everything were to fail at once? TRAC is your ally, helping you swiftly create a business impact analysis and establish a comprehensive business continuity program. Let TRAC be your guiding light through those turbulent moments of chaos.
What's Next?
Discover All TRAC Modules
TRAC adapts to your business needs with its suite of 11 modules that can work independently or tightly manage your risk with intermodular operability.
Certified TRAC Professional
Comprehensive understanding of TRAC methodologies, including all modules, their interactions, regulatory compliance, and interpretation of the data flowing out of TRAC.

