Your IT risk assessment is not just a routine check but a pivotal tool in shaping a robust information security program. Beyond merely developing policies or enhancing your security framework, a thorough IT risk assessment empowers your organization to make informed, strategic decisions that align with your security objectives. However, the effectiveness of an IT risk assessment hinges on certain critical features. Properly cataloging your assets, threats, and controls in your IT risk assessment is essential for pinpointing organizational risks, determining their origin, and strategizing appropriate mitigation actions.
Comprehensive Asset Identification for Effective Risk Management
To ensure comprehensive risk coverage, it's vital to include all IT assets in your assessment, regardless of whether they are hosted internally or externally. It's a common misconception that the security responsibility for externally hosted assets, like those at data centers, shifts away from your organization. On the contrary, it remains your responsibility to verify that external partners protect your data to your standards.
To ensure your IT assets are protected appropriately, you must review those protections through your IT risk assessment. One of the more important decisions your risk assessment can help you make is whether to risk assess a certain IT asset, such as a locally installed software, server, workstation, web application, online banking product, or wireless internet.
When defining an IT asset in the IT risk assessment, there are three components to identify:
- Hardware
- Operating system
- Application
IT assets may include only one of those three components, multiple components, or all three. For example, a server or workstation is a combination of hardware and an operating system, but the software and applications on the server or workstation will be assessed individually as separate IT assets.

IT Risk Assessment module in TRAC.
When identifying IT assets, you should also consider how valuable that IT asset is to your organization. At SBS, we call the value of an IT asset the "Protection Profile" in our risk management software, TRAC. Not all assets need to be given the same amount of attention or mitigation. A Protection Profile, as shown in the image below, can help determine how important an asset is and allow the organization to set different expectations for more important assets with a higher Protection Profile compared to assets with a lower Protection Profile. This is valuable in allowing you to prioritize the extremely important assets and handle highly sensitive customer information.
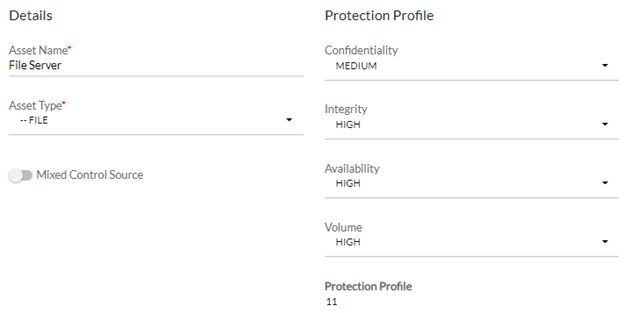
The Protection Profile of an IT asset in TRAC.
Enhanced Threat Identification and Impact Analysis
Addressing threats is done very differently amongst risk assessment tools, and how the tool handles threats may be a major determining factor in how well your risk assessment helps guide and improve the organization's risk structure. If threats are not detailed properly, you are probably not considering a wide enough scope for your mitigating controls.
For example, if you are only considering a couple of threats, such as malware or ransomware, your scope of remediation and controls to consider within the risk assessment will likely be limited to controls mitigating risk to those threats, such as your antivirus and firewall. While those are important threats to consider, your IT risk assessment should have a comprehensive list of all types of threats. A more detailed listing of threats that consider attack vectors that may be more physical in nature, such as theft, or threats that target the system through your employees, such as social engineering or phishing, can help expand that scope so that the risk assessment doesn't have a limited focus.
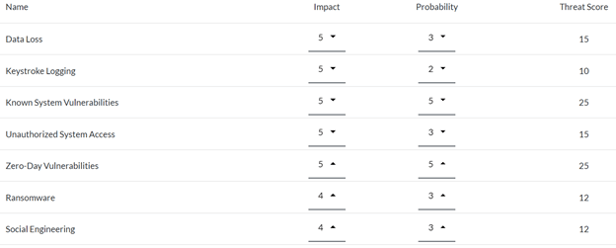
The Threat Score of an IT asset in TRAC.
Controls Frameworks and Future Risk Management
When your IT risk assessment captures a broad spectrum of threats, it naturally facilitates a more detailed control framework for mitigating them. More importantly, a detailed assessment helps you not only recognize currently implemented controls but also identify gaps in your control environment (excluded controls) and pinpoint additional controls needed for future security enhancements (future controls).
As an information security officer, you should be able to describe your plans to address the risks identified in your risk assessment to the board of directors. Perhaps you added the implementation of security information and event management (SIEM) to your strategic plan to mitigate risk for assets on your network, addressing an over-exposure of risk for workstations and servers. Perhaps your mitigation plan is more complex and includes a list of smaller controls, such as enforcing strong passwords on your most critical IT asset, reviewing activity and access logs on workstations, or enabling a session expiration on an important software application.
Either way, identifying what you are not doing and what you would like to do is especially important when determining the next steps for risk mitigation or resolving security issues with your network. Figuring out what to do next becomes more difficult when your IT risk assessment only includes the controls you currently implement.
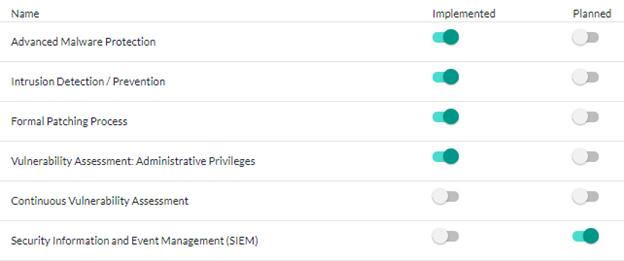
The implemented and planned controls for an IT asset in TRAC.
Developing a Proactive Risk Mitigation Strategy
One of the most important uses of an IT risk assessment is to constantly improve your security posture and identify where your biggest weaknesses lie. If one piece of your IT risk assessment truly helps you make decisions, it's your risk mitigation strategy. Establishing your risk mitigation strategy allows you to set goals for the organization, specifying an expected mitigation percentage for your IT assets based on the importance of the asset (Protection Profile).
For instance, equating the risk mitigation efforts for a basic office printer with those for a system handling sensitive customer data would be impractical and inefficient. Systems with high-value data demand more stringent mitigation efforts due to their elevated Protection Profile. This approach not only fosters continuous improvement in your security practices but also effectively identifies and excludes inadequate assets from your network. If a potential IT asset fails to meet the required mitigation thresholds during risk assessment, you have clear options:
- Exclude the asset due to insufficient risk mitigation capabilities.
- Enhance the asset's security measures to meet your standards through additional controls like password protection, logging, and session management.
These choices prevent the integration of insecure assets into your environment, reinforcing your overall network security.
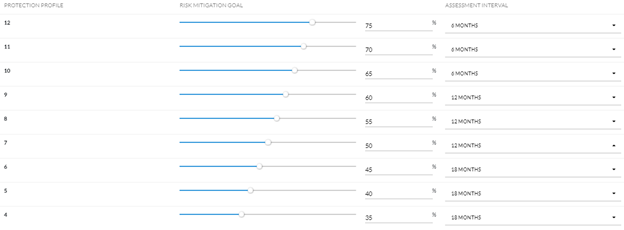
The risk mitigation goals and assessment intervals for IT assets in TRAC.
Recognizing your risk and identifying improvements, whether for a single standout asset or across multiple assets, is incredibly valuable. An organization should always know what its next focus is when it comes to IT risk mitigation. Once you get past the major risk outliers, how do you determine what that focus might be?
Addressing Remaining or Residual Risk
The assets with the highest residual risk will be the riskiest assets at the time of completing your risk assessment, making them prime targets for further mitigation. Although assets with high inherent risk scores are important, they may already have substantial controls in place, significantly reducing their residual risk. As a result, inherent risk scores are less useful for prioritizing mitigation efforts and funding allocation.
Residual risk metrics offer a straightforward and manageable way to communicate risk priorities to nontechnical stakeholders, such as the board of directors or senior management. Because residual risk is a universally understandable concept, it is an ideal focal point for discussion about risk assessment outcomes.
Additionally, calculating the percentage of risk that has been mitigated — from inherent to residual — offers a tangible measure of how effective your controls are. This metric is vital for evaluating whether the level of risk remaining within an IT asset aligns with your organizational risk appetite. When presenting these findings, emphasize the Protection Profile, residual risk, and mitigation percentage. These indicators are essential for directing future investments in risk management, ensuring that every dollar spent on mitigating risks is both strategic and justified.
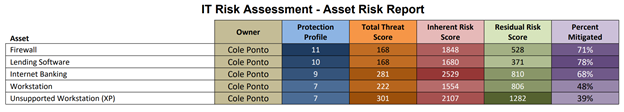
The Asset Risk Report in TRAC.
These discussions not only inform budget allocations but also ensure that executive leadership fully understands the rationale behind proposed security expenditures, optimizing resource allocation and strategic security planning.
Make the Right Decisions with SBS CyberSecurity
As you refine your IT risk assessment processes, remember that the insights gained are pivotal not only for improving your security posture but also for aligning your IT strategies with broader business objectives. By understanding and applying the principles of risk mitigation and residual risk management, you can make informed decisions that safeguard your organization’s assets and enhance its operational resilience.
At SBS CyberSecurity, we provide comprehensive tools and resources to support your risk assessment needs. Our TRAC risk management software offers a robust framework to streamline your processes with prebuilt elements that eliminate the complexity of starting from scratch. Unlike traditional spreadsheets, our solution simplifies workflows, reduces manual effort, and provides consistent, accurate data management. With an intuitive interface and features designed to address real-world challenges, TRAC can empower your organization to meet regulatory requirements, strengthen your security posture, and make smarter, data-driven decisions faster and more efficiently.
Investing in a thorough IT risk assessment is not just about compliance — it's about building a resilient future for your business. Let us help you turn your IT risk challenges into opportunities for security enhancement and strategic growth.
![]()
IT Risk Assessments

Your company and your information technology needs are unique. Discover the impact of a customized audit that goes beyond a simple IT checklist.
Read More
TRAC was built to help you easily demonstrate compliance while also giving you the information you need to make the best decisions for your organization.
Read More


.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
