SBS CyberSecurity has been made aware of a new type of phishing attack involving web3 or blockchain front ends and websites. Blockchain web front ends, such as https://etherscan.io/ for the Ethereum blockchain, exist to help customers with blockchain transactions, accounts, and smart contracts. Terminology to be familiar with for this advisory include the terms “web2” and “web3.” Web2 is the term used to identify any web technology that does not use blockchain’s distributed ledger encryption technology. Alternatively, web3 is any web technology that uses distributed blockchain ledger encryption technology.
The Microsoft 365 Defender Research Team, who coined the term “ice phishing,” states:
“There are multiple types of phishing attacks in the web3 world. The technology is still nascent, and new types of attacks may emerge. Some attacks look similar to traditional credential phishing attacks observed on web2, but some are unique to web3. One aspect that the immutable and public blockchain enables is complete transparency, so an attack can be observed and studied after it occurred. It also allows assessment of the financial impact of attacks, which is challenging in traditional web2 phishing attacks.”
There are more definitions for web3 terminology available from Microsoft.
Who Can Be Affected?
The attack affects anyone who uses web3 blockchain front ends or websites.
How Does This Attack Work?
Web2 credential compromise is very similar to web3 cryptographic key disclosure. Attackers can phish for users of web3 to disclose the cryptographic keys. Disclosing those keys to an unauthorized party can grant the attacker the capability to move your funds without your consent. The attackers can phish the same way through phishing emails, but this tactic is not optimal. Other tactics they are using include but are not limited to:
- Monitoring social media for users reaching out to wallet software support and jumping in with direct messages spoofing support to steal one’s private key directly
- Distributing new tokens for free to a set of accounts (i.e., “Airdrop” tokens), and then failing transactions on those tokens with an error message to redirect to a phishing website6 or a website that installs coin mining plugins that steal your credentials from your local device
- Typosquatting and impersonating legitimate smart contract front ends
- Impersonating wallet software and stealing private keys directly
Ice phishing, however, refers to a specific type of phishing that tricks the user into signing a transaction that delegates approval of the user’s tokens to the attacker. Microsoft’s Defender team put out these excellent graphics detailing the attack:
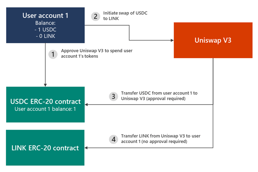
Figure 1: Uniswap example flow
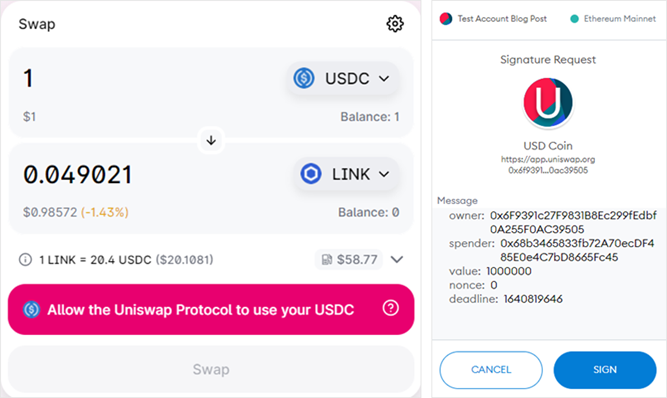
Figure 2 - Uniswap approval interface. Figure 3 - Approval transaction signature request.
In an ice phishing attack, the attacker just needs to modify the sender address to the attacker address. Microsoft states: “This can be quite effective as the user interface doesn’t show all pertinent information that can indicate that the transaction has been tampered with.”
What Can You Do?
As always, SBS recommends training employees in security awareness and testing them with phishing; however, these attacks put the employees that monitor and perform these business transactions with your crypto at the top of the list of high-risk employees. Additional training and controls should be implemented to handle high-risk employee situations. Some of those controls include tighter user access privileges (principle of least privilege), Multi-Factor Authentication (MFA), Privileged Access Management (PAM) if the user’s access is considered “elevated” or administrator-level, additional logging and monitoring around such user accounts, and stronger passwords than the average user. However, most of those controls don’t do much to prevent web3 attacks in web3 app front ends. Separation of duties and dual controls can work great for web3 app front ends. Microsoft points out some other effective and specific controls:
- Review the smart contract with which you are interacting.
- Is the contract address correct? Unfortunately, one can’t rely on the smart contract front-end to interact with the proper smart contract. The contract address that appears in the transaction to be signed needs to be inspected before the transaction is submitted. This is an area where wallet providers can innovate and add a layer of security.
- Has the smart contract been audited? Several websites can help with that assessment, such as defiyield.
- Is the contract upgradeable (in other words, is it implemented as a proxy pattern) such that the project can deploy fixes when bugs are uncovered? Etherscan’s contract tab shows whether a smart contract has been implemented as a proxy.
- Does the smart contract have incident response or emergency capabilities, like pause/ unpause? Under what conditions are these triggered?
- What are the security characteristics of the smart contract after deployment? CertiK Skynet tracks post-deployment security intelligence through on-chain monitoring.
- Manage your cryptocurrencies and tokens through multiple wallets and/or periodically review and revoke token allowances. https://etherscan.io/tokenapprovalchecker makes doing this easy.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)

