Should Users Have Local Admin Rights? The Danger of Local Administrative Privileges

Users enjoy the freedom of having local administrative rights on their workstations. They can add/remove programs, install printers, etc., without requiring assistance from the IT department. In a small organization with limited IT resources, granting users local admin rights allows IT to focus on more important projects. However, convenience often comes at a cost.
If an attacker compromises a user account with local admin privileges, it could spell disaster for an organization. Would you want to give hackers the ability to do any of these things?
- Disable endpoint antivirus
- Install malicious software
- Encrypt data with ransomware
- Move laterally within a network
- Generally weaponize the system against the organization
During a recent internal penetration test, our network security team demonstrated how an attacker could leverage an account with local admin privileges to take over a domain. Using various attacks, we were able to compromise a regular user account and password. Using a tool named CrackMapExec, we then determined the stolen account had local admin rights on two devices on the network.
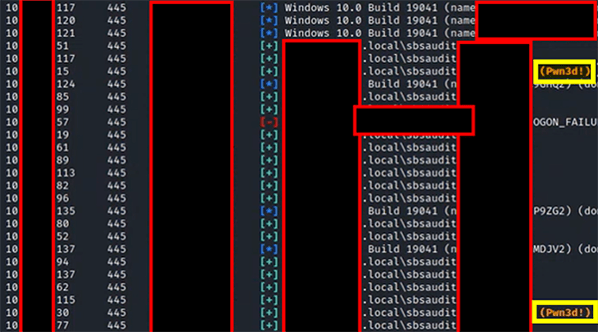
The same tool allowed us to download local password hashes of local accounts on those devices.
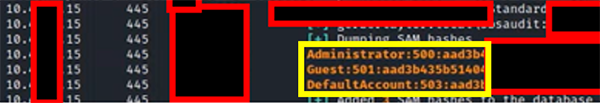
Attackers don’t even have to crack these encrypted hashes in order to use them. CrackMapExec allows attackers to pass local account hashes to other devices to determine what access levels they may have.
Here’s the worst part: One of the two devices that our compromised account could access with local admin rights was the client’s Primary Domain Controller. Accessing this server with the local admin account meant we had found the keys to the kingdom, effectively giving us complete administrative access to ALL domain resources.
Benefits of Removing Local Admin Rights
Removing local admin access might not be well received by users. However, doing so provides many benefits to an organization’s security posture:
- Lowers risk of malware infections
- Ensures antivirus and other protections remain active
- Reduces an attacker’s ability to exploit vulnerabilities
Special Circumstances
Most employees do not need local admin access to perform their daily job duties. However, some users may occasionally require higher privileges to complete a task. For these situations, it is recommended to create a separate account with admin-level access. The employee should only use the privileged account when necessary to complete their work.
Another alternative is to discover what privileges to which folders, executables, and registry keys the legacy software preventing the organization from removing local admin privileges requires. This can be done with Diskmon from Sysinternals. The user account can then be customized to have admin access to just the required items, removing the business need for local admin privileges.
The Answer? Lock it Down
Granting users local admin access was a common practice in the past. However, modern security threats require IT professionals to move beyond the mindset of “this is how we’ve always done it.”
The risks associated with local admin access far outweigh the convenience benefits. Remove local admin access from your users before hackers take advantage of this unsafe, outdated practice.
![]()
How Can SBS Help?
Discover the true strength of your network’s security by putting it through the ultimate test with a Network Security Audit. Partner with SBS to run a strategic combination of testing services that simulate a real-world attack scenario, providing a comprehensive assessment of network security.
![]()

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
