Microsoft announced two new zero-day flaws in Exchange Server on September 29, 2022. If you host your own Exchange server, these are extremely critical mitigations to perform.
Microsoft said it is investigating two reported zero-day flaws affecting Microsoft Exchange Server 2013, 2016, and 2019. CVE-2022-41040 is a Server-Side Request Forgery (SSRF) vulnerability that can enable an authenticated attacker to remotely trigger the second zero-day vulnerability — CVE-2022-41082 — which allows remote code execution (RCE) when PowerShell is accessible to the attacker.
Who Can Be Affected?
Anyone hosting their Exchange server and not in the MS365 cloud can be affected by these vulnerabilities. Microsoft said Exchange Online has detections and mitigation in place to protect customers. Customers using on-premises Microsoft Exchange servers are urged to review the mitigations suggested in the security advisory, which Microsoft says should block the known attack patterns.
How Does This Attack Work?
Attackers use obfuscated webshells dropped on the Exchange servers. Attackers use a webshell management platform to manage the webshells. Most exploits are thought to be a Chinese attack group APT. If you recall the Hafnium attacks of American and German Exchange servers in March 2021, this seems to be a similar group with a similar attack capability.
Microsoft is quick to point out that these zero-day flaws require an attacker to have a valid username and password for an Exchange user, but this is easy for attackers to socially engineer with fake login and landing pages.
What Can You Do?
Microsoft released a blog with mitigation recommendations. The blog is up-to-date with additional items Microsoft finds as the threat progresses, so check back often.
Exchange Online customers do not need to take any action.
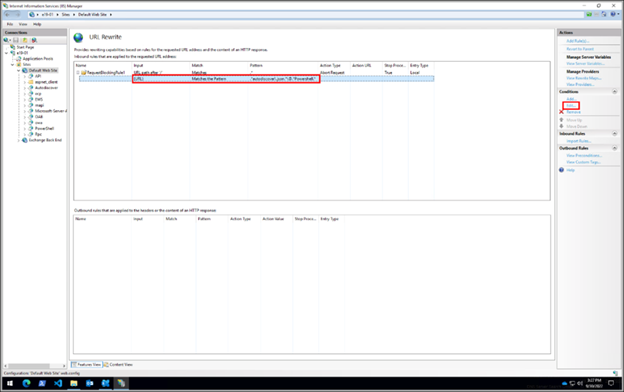
The current Exchange Server mitigation is to add a blocking rule in “IIS Manager -> Default Web Site -> URL Rewrite -> Actions” to block the known attack patterns. Exchange Server customers should review and choose only one of the following three mitigation options.
- Option 1: For customers with the Exchange Emergency Mitigation Service (EEMS) enabled, Microsoft released the URL Rewrite mitigation for Exchange Server 2016 and Exchange Server 2019. The mitigation will be enabled automatically. Please see this blog post for more information on this service and how to check active mitigations.
- Option 2: Microsoft created a script for the URL Rewrite mitigation steps.
- Option 3: Customers can follow the below instructions, which are currently being discussed publicly and successfully break current attack chains.
- Open IIS Manager
- Select Default Web Site
- In the Feature View, click URL Rewrite
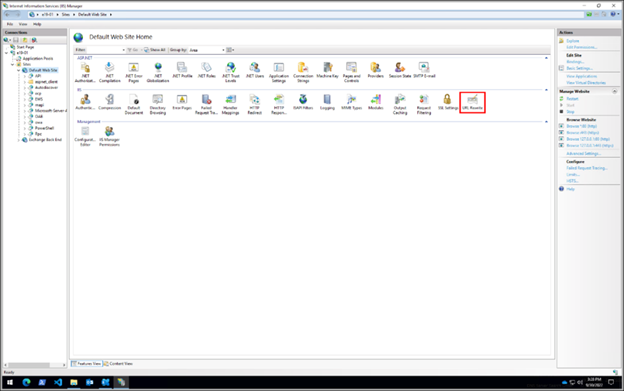
- In the Actions pane on the right-hand side, click Add Rule(s)…
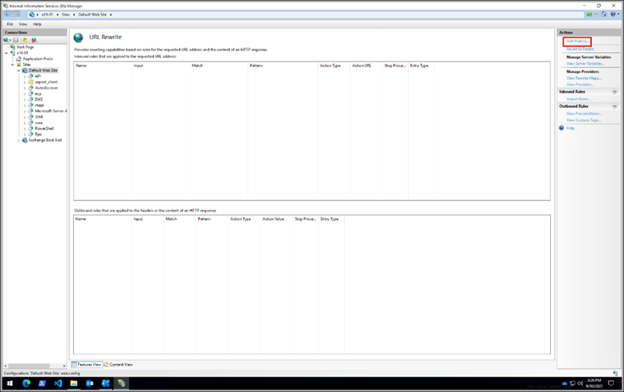
- Select Request Blocking and click OK
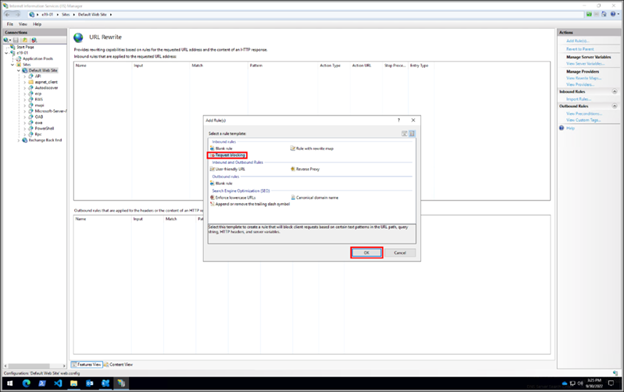
- Add the string: .*autodiscover\.json.*\@.*Powershell.*
- Select Regular Expression under Using
- Select Abort Request under How to block and then click OK
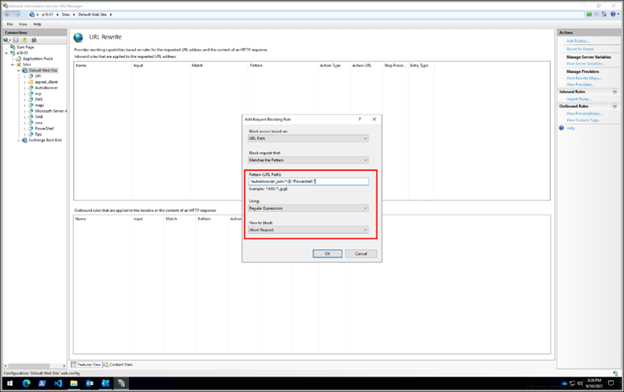
- Expand the rule and select the rule with the pattern .*autodiscover\.json.*\@.*Powershell.* and click Edit under Conditions
- Change the Condition input from {URL} to {REQUEST_URI}
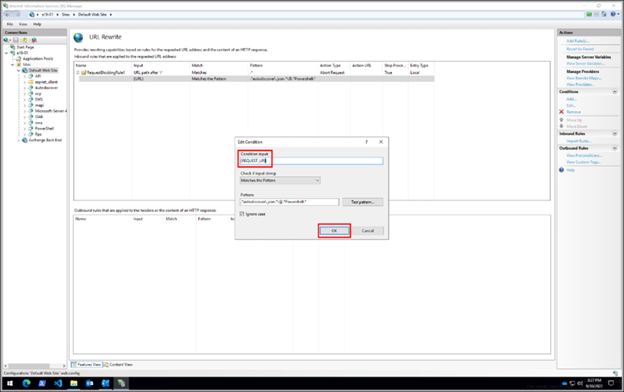
NOTE: If you need to change any rule, it is best to delete and recreate it.
Impact: There is no known effect on Exchange functionality if URL Rewrite is installed as recommended.
We strongly recommend Exchange Server customers disable remote PowerShell access for non-admin users in your organization. Guidance on how to do this for single user or multiple users is available here.
Detection and Advanced Hunting
For detection and advanced hunting guidance, customers should reference Analyzing attacks using the Exchange vulnerabilities CVE-2022-41040 and CVE-2022-41082.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)

