The LockBit 2.0, formerly LockBit, ransomware group was active in Q2 2021. After a slight dip in activity in August, the group is back now with its Ransomware-as-a-Service (RaaS) affiliate model. According to the Prodaft threat intelligence team, the group was previously called ABCD Ransomware and operated a similar affiliate program.
This is especially critical because the group just ransomed a bank in the Midwest region. This is what we know about the group:
- LockBit 2.0 is a financially motivated actor and, with the recent shut down of REvil and BlackMatter, they have become one of the largest and most successful ransomware operations currently running.
- They are constantly adjusting tactics.
Who Can Be Affected by LockBit2.0?
Any business can be affected, but we are seeing an increased surge against financial institutions.
How Does This Attack Work?
- LockBit often gains network entry using compromised Remote Desktop Protocol (RDP) or VPN accounts that have been leaked or stolen. LockBit has also attempted to recruit insiders to help gain access through legitimate login credentials.
- LockBit has used Ryuk's Wake-on-LAN feature, sending packets to wake offline devices to help move laterally around networks and compromise as many machines as possible.
- LockBit uses a tool previously deployed by Egregor ransomware, using printers on the network to print out ransom notes.
What Can You Do?
RDP Protocol
- Make sure that your organization isn’t publishing RDP access to the Internet through your firewalls or presenting it raw to the Internet.
- If your organization does have RDP presented to the Internet for a real business purpose, monitor for RDP brute force attacks Windows Log Event ID 4625 failed login attempts. You will see tens or even hundreds of logs generated per second., This is likely too many for Windows to log along with the error code denoting that Windows cannot keep up with logs since too many are happening simultaneously. If you see that activity, block the originating IP and keep monitoring. Attackers can switch their IP, so this process might be lengthy.
- Monitor for Windows logs showing East to West RDP connections IDs - Windows Log Event IDs 1146, 1147, 1148, 1149, 4624 and 4625 Type 3, if out of the norm.
VPN Protocol
- Monitor for impossible travel, atypical connection activity, and new connection activity from a known VPN user. This will help look for the attackers attempting to connect. Remember, this group likes to attempt recruiting insiders, so exempt no one from this monitoring.
Wake-on-LAN (WOL)
- Turn off WOL if it is not needed for your network. If needed for a business purpose, monitor WOL logs for unknown or unexpected activity.
Printers
- Printers often have many services to establish all the connectivity types a business could ever need. Your organization probably needs as few as one of these services, so disable the rest. This will also help cut down on network chatter that can often degrade network performance (if your organization has many printers) and bury legitimate traffic when watching packets with a tool like Wireshark or TCP Dump.
Security Awareness Training (SAT) and Phishing Test
- SAT and phishing tests should be performed so your users know how to spot credential stealing techniques. Tools like KnowBe4 and PhishMe are fantastic solutions.
This isn’t an exhaustive list of things to monitor and watch for, just things specific to this group. However, SBS CyberSecurity has documented the following indicators of compromise (IoCs) that are general to all modern ransomware attacks to best prepare your organization.
Indicators of Compromise
The image below is the flow of a modern ransomware attack. Within the flow, we break down the attackers’ kill chain (techniques and processes they perform to get to the result of ransomware).
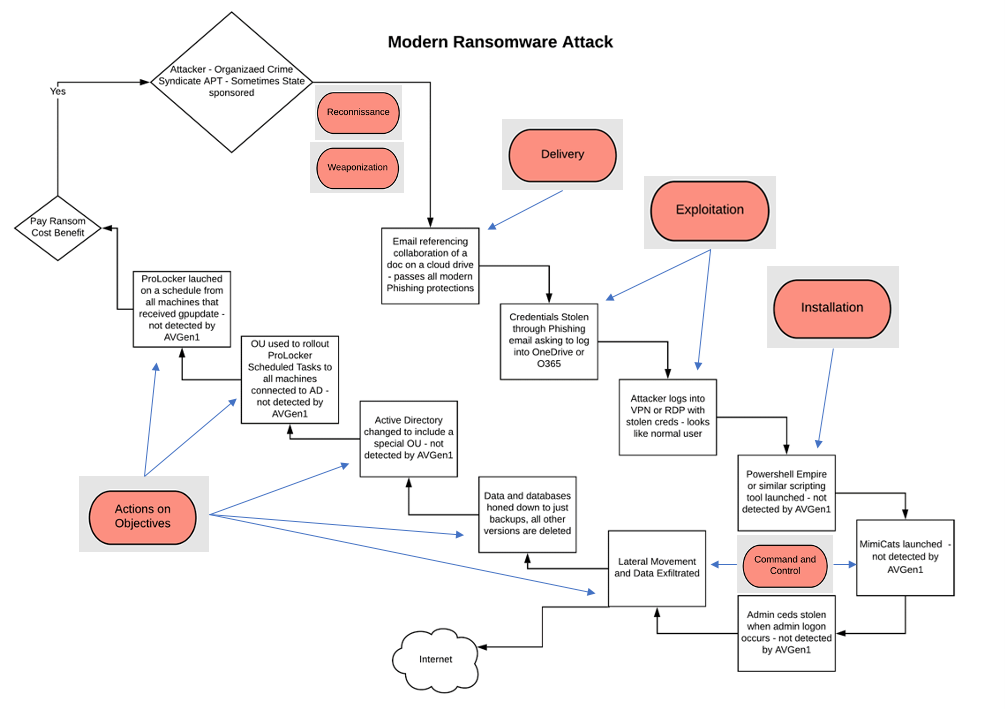
It's essential to be aware of the following indicators of compromise common to all modern ransomware attacks so your organization knows what to look for and how to be best prepared to defend your data.
Recon
- Scanning of your network and cloud assets.
- Emails phishing for information.
- Strange phone calls phishing for information.
Delivery
- Phishing emails with actionable items.
- Phone calls with actionable items.
- Scanning specific ports or an abundance of scanning on a particular port or set of ports or IPs.
- Brute force authentication requests on external exposed services.
Exploitation
- Logins or attempted logins at strange times - user heuristics.
- Impossible travel logins from other geographic locations.
- Logins or attempted logins from new or unknown IP.
- Strange IPs or DNS requests originating from inside your network or cloud resources.
- Persistent connections to new or unknown IPs.
Installation
- Scripting running from non-IT resources.
- Unknown scripts running in the environment.
- Persistent connections to unknown IPs.
- Creation of new AD accounts.
- Elevation of current AD accounts.
- Use of service accounts for other tasks out of the norm.
- Logs showing East to West RDP connections IDs (Windows Log Event ID) 1146, 1147, 1148, 1149, 4624 & 4625 Type 3, if out of the norm.
Command and Control
- Unknown or abnormal DNS requests.
- Persistent connections to unknown IPs.
- Large or sustained data flows out of your network of cloud resources.
- Use of service accounts for other tasks out of the norm.
- Creation of new AD accounts.
- Logins or attempted logins at strange times - user heuristics.
- Impossible travel logins from other geographic locations.
- Logins or attempted logins from new or unknown IP.
Actions on Objectives
- Historical backup deletion.
- Historical database deletion.
- Unexpected backup changes.
- Unexpected database changes.
- Unexpected AD changes especially new OUs or changes to Group Policy.
- Changes to scheduled tasks or new scheduled tasks.
- Any IoCs from the Command-and-Control phase can also occur here.

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)

