Who Can Be Affected?
Anyone running Exchange internally that hasn’t patched the following CVEs.
- CVE-2021-34473
- CVE-2021-34523
- CVE-2021-31207
*Note that as the attacker and their platform for automated attacks evolve, the CVEs they can exploit may expand.
How Does This Attack Work?
The FIN7 group is using an automated system called Checkmarks with the above CVEs and their custom code to discover vulnerable Exchange servers and gain access to victims’ networks using web shells. We saw a similar approach to this in March 2021 with the hacker group Hafnium.
Since June 2021, FIN7 has upped their game and automated their web shell attacks against Exchange servers with custom code and a tool called Checkmarks. Checkmarks uses the Django framework and allows the attacker to test for vulnerabilities in code and then manage those vulnerabilities. The group also uses SQLMap, through the Checkmarks Auto SQL Module, to help map the SQL environment and scan for SQL vulnerabilities. Their custom code links these systems together and automates target acquisition and processing. More information is below in the More About FIN7 Tech section.
What Can You Do?
The best thing you can do if you have Exchange in-house is to RELIGIOUSLY run the following procedure and patch your Exchange environment: https://www.stellarinfo.com/article/install-exchange-cumulative-updates.php.
Keeping abreast of Exchange vulnerabilities is also a MUST. This Microsoft Security Response Center blog addresses them as Microsoft becomes aware of them.
Additionally, there is more information in this section More IoCs.
Extended Information
The following information has been pulled directly from the Prodaft report. Prodaft owns all rights and information.
More About FIN7
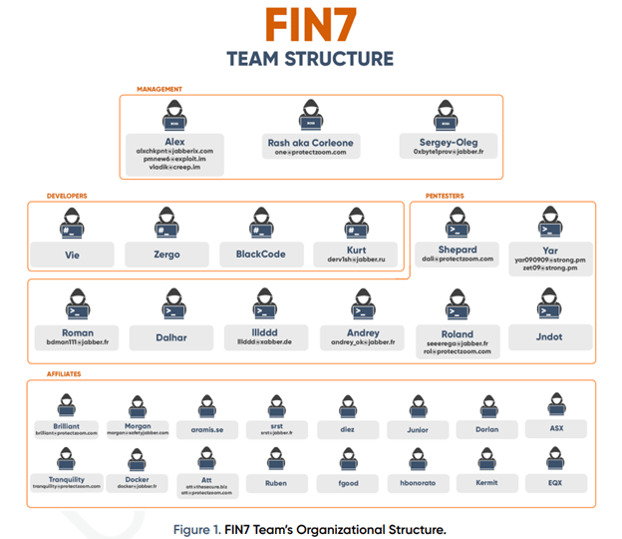
The FIN7 team has an interrelated structure that ensures consistent workflow among the team members throughout each operation. In Figure 1, the internal management is demonstrated hierarchically whilst revealing precisely tailored inner structures. Moreover, this section focuses on interactions among the group members and clearly indicates individual responsibilities and practices that each member engages in.
More About FIN7 Tech
The FIN7 hacking group often uses custom scripts to exploit public-facing web applications. In conversations between group members as shown in below, they have discussed using the CVE-2020-0688 vulnerability in Microsoft Exchange applications to run arbitrary PowerShell scripts on victims’ servers. This allows them to gain unauthorized access and potentially steal sensitive information.
Before using the exploit for CVE-2020-0688 vulnerability, the FIN7 group checks whether or not the vulnerability exists on the victim servers. Thereon the PTI team found the README file describing this operation for Exchange servers on detecting vulnerability.
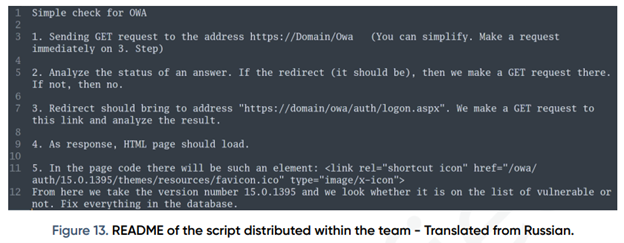
With aforesaid, for using exploit against Exchange vulnerability, this threat group purchases the stolen accounts of OWA on specific internet markets, and examines their validity. A file README is given below with commands of Python-script for checking accounts (see Figure 14).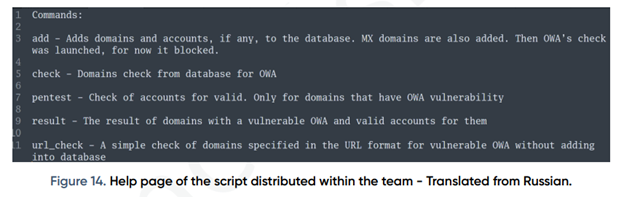
In addition to the CVE-2020-0688 vulnerability, the FIN7 team members were quite interested in other types of Microsoft Exchange exploits, including ProxyLogon, ProxyShell, or CVE-2021-42321. To take advantage of these vulnerabilities, they developed tailored scripts to automate the exploitation process. They customized public exploits and sometimes combined them with zero-day vulnerabilities to create even more effective attacks. It’s likely that they decided to develop a new system to automate this process, and they created the tailored system (as described in Section 4.4) for that purpose. This system allowed them to quickly and efficiently exploit any vulnerable systems they came across.
In addition to the tactics and techniques they have already been known to use, the PTI team has discovered that FIN7 is also affiliated with ransomware groups such as REvil, LockBit, and Darkside. One of the ways they infiltrate victim networks and subsequently encrypt their devices is by purchasing stolen authentication data, such as VPN, RDP, Firewall, Email accounts and other access types used by enterprises. These accounts are typically stolen by stealer malware and sold on underground markets, where FIN7 and other threat actors can purchase them. This allows them to gain access to a wide range of systems and carry out their attacks more easily.
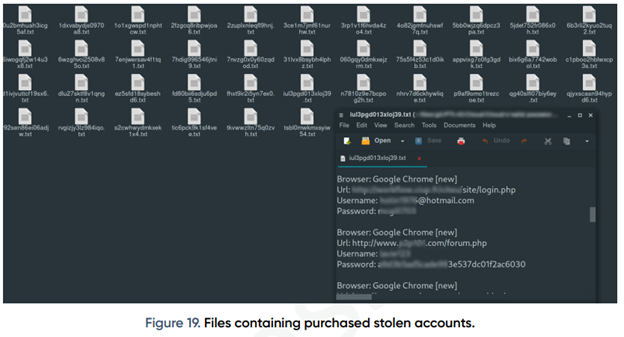
The FIN7 group carefully scrutinizes the validity of stolen accounts and uses a service like Zoominfo to select the firms and organizations with the highest revenue. Once they have gained initial access to these systems, they steal and encrypt files, and determine the ransom amount based on the company’s revenue. A sample file containing purchased stolen accounts can be seen in Figure 19. This file gives the threat actors access to all of the victim’s information, including their browser, website URL, username, and password. This allows them to carry out their attacks with precision and maximize their profits.
In order to maintain versatility and ensure access to as many channels as possible, FIN7 also commonly uses spear phishing as an attack vector. The group members distribute spam e-mails by demanding payment with an attached malicious file .docm. This file has a macro script which opens a backdoor in a victim’s device. Figure 20 depicts an example of a phishing text message sent via e-mail in the Italian language. It is translated as, ”Hello, Please pay the invoice; we have not yet received your payment. If the payment has already been sent, ignore this e-mail. Thank you.”
When the victim opens the attached document, a legitimate message appears that says "To see the attached document, click on Enable Content.” This allows the malicious script to be activated on the victim’s computer, opening a backdoor that allows FIN7 to silently gain access. This is a common trick that attackers use to trick victims into enabling the malicious content, allowing them to infect the victim’s device without their knowledge.
The PTI team noticed a unique system used by the FIN7’s sub-team that targets the Microsoft Exchange servers and other public-facing applications in particular by mass scale scanning. The deeper analysis revealed that the attackers directly scanned and exploited hundreds of Microsoft Exchange servers with Proxyshell (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) vulnerabilities. After the Proxyshell vulnerabilities were announced as part of the April 2021 Microsoft Exchange Server Security Updates[4], the first proof-of-concept (POC) examples of these vulnerabilities began to appear in August of that year. Most threat actors, including those deploying LockFile[1], Babuk[6], and QBot[7], first used these vulnerabilities in August and September 2021. However, our team discovered that FIN7’s initial operations using these vulnerabilities started in June 2021, before the public POCs were released. This indicates that FIN7 was actively monitoring the situation and was able to quickly take advantage of these new vulnerabilities to carry out their attacks. Threat actors exploit ProxyShell vulnerabilities to establish remote PowerShell sessions on the vulnerable Exchange Servers. There are several ways that attackers have used the PowerShell to create web shells.
Following vulnerabilities are observed to be exploited:
- CVE-2021-34473 : Microsoft Exchange Server Remote Code Execution(RCE) vulnerability that does not require any user action or privilege to exploit ;
- CVE-2021-34523 : Microsoft Exchange Server Elevation of Privilege Vulnerability after authentication ;
- CVE-2021-31207 : Microsoft Exchange Server security feature bypasses vulnerability flaw that allows attackers to gain administrative access.
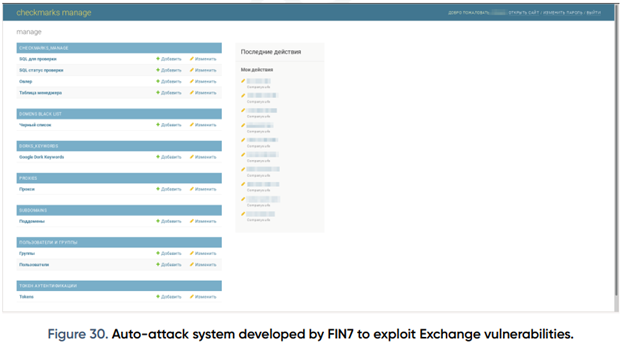
On June 1, 2021, the FIN7 team created an automated attack system called Checkmarks using the Django framework. They primarily used the system to scan for exchange servers and run Microsoft Exchange exploits on them, as seen in the screenshot in Figure 30. This allowed the team to identify and exploit vulnerabilities in exchange servers worldwide. The below table shows the details of the tailored system.

After the target domains are added to the panel, the scanner service uses the given IP addresses to scan the exchange server for OWA files. If an exchange server is detected in any of the domains, the exploit is applied and a shell is dropped over via Powershell. The panel not only performs exploitation, but also provides various details on the victim, as seen in Figure 31.
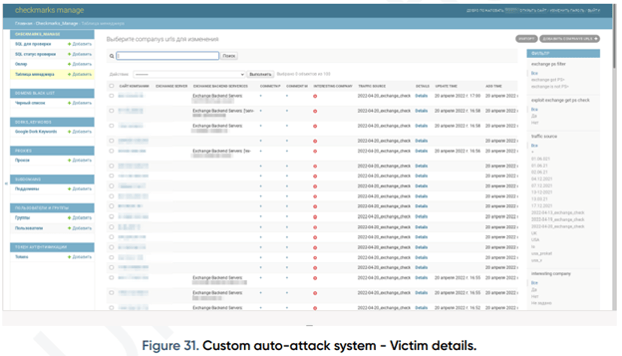
The Traffic Source is where the attack is made, and further it represents; the exchange vulnerability running status, the Powershell running status, and the shell release status. By looking at these sources, it is understood that the system accepts victim domains mostly from the USA, UK, and CA.
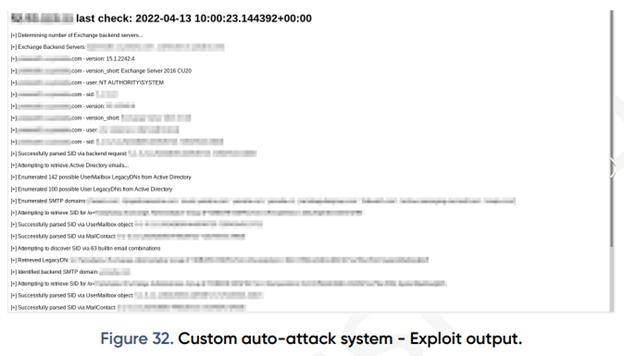
The FIN7 team successfully carried out exchange server attacks in June 2021 using a custom exploit code. However, this exploit was later removed from their panel. After September 4, 2021, they began targeting victims using an open source exploit[2], as seen in the log file in Figure 32. The image below shows a victim that has been successfully scanned and had a Powershell script run on it. When the Proxyshell attack is successful, post-exploitation steps are automatically executed, including extracting all emails from Active Directory (AD) and collecting all Exchange Server information.
After successful exploits are displayed on the main page, the FIN7 actors begin to examine each victim’s domain by filtering them with ’exchange got PS’. Simultaneously, the Pentest and Marketing teams collaborate with FIN7 on sharing information about their victims as shown in Figure 33.
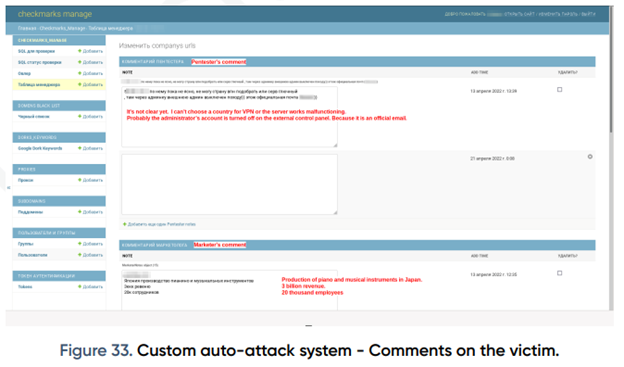
The Marketing team at FIN7 first gathers information on potential victims, including their current revenue, number of employees, headquarter details, domain, and website. They then share this information with the Pentesters to determine if the victim is a worthwhile target. If a firm is deemed to have a sufficient market size, the Pentester leaves a comment for the admin on how the server connection can be used, how long the attack can last, and how far it can go. This information is used to shape the next stages of the attack. This level of planning and coordination is not typical among other cybercrime groups and is a distinct characteristic of FIN7.
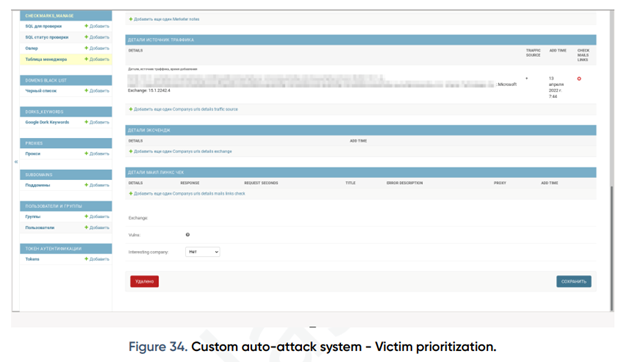
In the remaining section of the Victim company details page, there is a list of the relevant victims’ AD domains, along with their company URL details and mail information obtained from the exchange server, as seen in Figure 34. If the company meets the criteria for targeting, it will be flagged by the threat actor for the admin to see. This allows the FIN7 team to easily identify and prioritize potential victims.
Even more information at the Prodaft report Page 30 here: https://www.prodaft.com/resource/detail/fin7-unveiled-deep-dive-notorious-cybercrime-gang
More IoCs
Please see Prodaft’s full report, IOCs section, starting on page 51 for a full listing of IoCs.
https://www.prodaft.com/resource/detail/fin7-unveiled-deep-dive-notorious-cybercrime-gang
Extended Information
The following information has been pulled directly from the Prodaft report. Prodaft owns all rights and information:

.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)

