Remember Log4j… that December 2021 vulnerability that had us all doing a deep dive into our applications to seek out the critical vulnerability? Heading into late 2022, we can rest easy knowing that it has been put to rest, right? Well, not really.
If you recall, Apache's Log4j is a software library that logs certain events, such as user activities within Java-based applications. Log4j is open-source and freely used by an enormous array of applications worldwide. The remote code execution (RCE) vulnerability associated with Log4j, CVE-2021-44228, is critical because by successfully exploiting this vulnerability, an attacker can do anything they want, including the deployment of malware or ransomware. Data extraction or manipulation is possible for attackers with even novice technical skills through this exploit.
Since Apache's Log4j software is so widely deployed, there is no main list of applications associated with its use. In response, the Cybersecurity & Infrastructure Security Agency (CISA) launched a community-sourced GitHub repository to create a listing of vulnerable products: GitHub - cisagov/log4j-affected-db: A community sourced list of log4j-affected software.
The resources and time commitment required to track down each instance of Log4j within an environment, determine a resolution plan, and perform an eventual upgrade to the latest version can be enormous. While many organizations may be persistent with the identification and resolution efforts, Log4j remediation requires a substantial number of critical resources that organizations may find scarce when facing an onslaught of new security issues and competing projects. These organizations may not have reached a cyber maturity level to fully leverage the benefits of a dedicated CIO or CISO within their organizational structure. The absence of a defined, responsible individual overseeing the information security program will likely mean a shortcoming in vulnerability resolution.
Taking this reality into consideration, the Cyber Safety Review Board (CSRB) concluded that the outdated and vulnerable instances of Log4j will continue to be exploited over the next ten years and possibly beyond. So far, exploitation has been relatively low, but the opportunity will remain available for attackers for the foreseeable future. If you are unfamiliar with the CSRB, President Biden directed the establishment of the CSRB to review significant cyber incidents and provide "advice, information, or recommendations for improving cybersecurity and incident response practices and policy."
A few observations from the CSRB report include:
- Adopt industry-accepted practices and standards for vulnerability management and security hygiene.
- Drive a transformation in the software ecosystem to move to a proactive model of vulnerability management.
- Vendors like one cybersecurity technology services company observed the use of botnets to automate the reconnaissance process to quickly identify vulnerable targets.
- A cybersecurity technology services company investigated multiple ransomware incidents that leveraged the Log4j vulnerability from January 2022 through March 2022.
The full CSRB report can be found here.
As always, follow your risk assessment program to determine your organization's best course of action. Part of your risk assessment may include identifying whether a vulnerable device is exposed to being attacked. Compensating controls may reduce exposure.
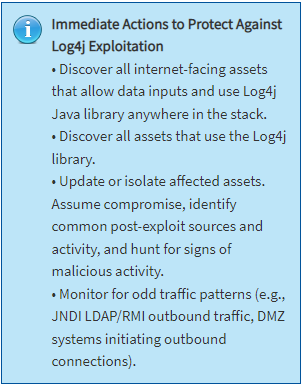
If you are uncertain of your position, CISA offers this guidance:


.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
