We have covered Business Impact Analysis in a previous blog post, diving into information on what should be included within a good BIA. While the creation of a proper Business Impact Analysis is important, something that many organizations can improve is the utilization of the Business Impact Analysis and the results pulled from this assessment. While your BIA needs to meet regulatory expectations, it’s even more important that your BIA and the business process information you build out is used to mitigate additional risk for the organization.
Business Impact Analysis
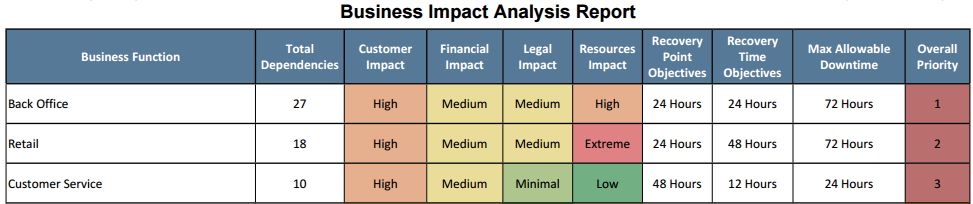
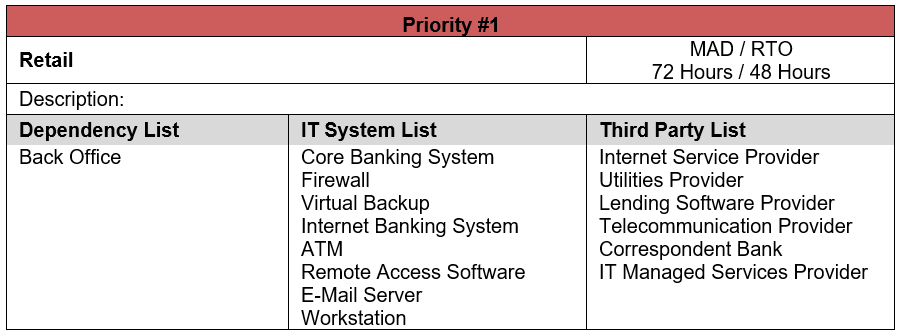
The primary function of the Business Impact Analysis is to identify your business process recovery priorities (example below). However, a ton of data is input to receive such a report, and certainly more can be gleaned from the process than a simple prioritization list. Much of the data that you can use to make better decisions and mitigate additional risk is going to come from business process dependencies. As a reminder, the TRAC process takes into account other business processes, vendors, and IT assets that a business process relies on to function, which can be pretty valuable information.
Using Dependency Data
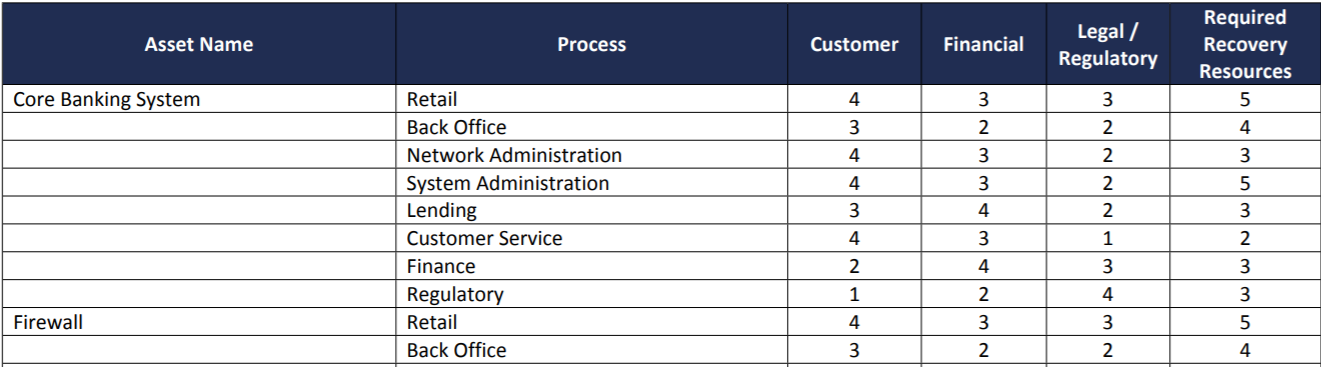
The three (3) variables considered as part of our dependencies are all important; however, we can take more valuable data from some than others. For example, identifying the business processes that rely on one another is incredibly important for determining priority, but the use of that data outside of priority calculation can be pretty limited. Vendor and IT asset dependencies, on the other hand, are a very different story. So, after enumerating all the IT assets that each of your business processes require to function, how can you use this information to mitigate additional risk?
- Testing Schedule: If the most critical IT assets can be identified for each business process, this information can be used to develop a testing schedule. This information can show what assets are consistently required for business operations and which assets should be prioritized in live disaster recovery testing, tabletop testing, or backup testing.
- Redundancy Planning: Identifying IT asset redundancy becomes easier when you can see how many processes an asset is associated with. Even more, if one of your critical IT assets cannot be purchased, configured, and placed online in a secure and complete manner before reaching the Max Allowable Downtime timeframe, this may be an indication that the noted IT asset is a prime candidate for redundancy.
- Procedure Development: Depending on size and complexity, many organizations do not have a recovery procedure built out for every application and system used. Identifying your most critical IT assets can assist in determining which applications and systems should have a system and application recovery procedure documented. Your most critical IT assets can be identified by seeing which assets are assigned for our top priority business process in conjunction with how many other processes require that asset.
With vendors being a major part of your Business Continuity Plan, it’s not just IT assets that organizations need to plan around. You can use vendor dependency information in a very similar manner as the IT asset dependencies were used; however, there are going to be some differences.
- Contact List Development: Any vendor that a business process is dependent upon should be added to your contact list and included in your Business Continuity Plan.
- Tabletop Testing Development: Service Provider Unavailability is not only a great threat to have included within your BCP risk assessment, it is also frequently one of the more inherently risky threats noted in a risk assessment, due to its higher probably and significant impact. If one of your critical vendors is unable to provide you with a service your organization (and your customers) relies on, the impact to your organization can be enormous. When planning for your BCP tabletop scenarios, take some of your most frequently-listed vendor dependencies and develop a testing scenario around one of those vendors being unavailable for an extended amount of time. For example, many internet service providers, internet banking providers, and even core processors (looking at you, Finastra) have experienced cyber-incidents, outages, or bandwidth issues during this COVID-19 pandemic. How have these situations impacted your organization?
- Redundancy Planning: In the same way you plan for maintaining redundant IT assets, you need to consider the potential for redundant vendors. A common example is your internet service provider (ISP). If a vendor’s unavailability has a widespread impact across all or most of your business processes, depending on the vendor in question, a backup service provider could be a huge risk mitigation.
Beyond BIA’s Core Purpose
When an organization puts effort into gathering so much data to create a valuable Business Impact Analysis, the idea that you are only going to use that data to get a listing of most-important to least-important business processes can be pretty disappointing.
The good news is that you are only limited by your creativity when it comes to how you can use your BIA to both create and improve the business continuity planning process. Even more so, with the amount of detail that goes into building a proper BIA, organizations often run into other areas of the Information Security Program that can be improved. When going through your dependencies, you may find an IT asset that hadn’t been properly added to the IT risk assessment. Perhaps you’ll identify a vendor whose availability rating may need to be increased, or maybe even a vendor that was missed in your vendor management process.
If you are a user of TRAC, you will notice that IT asset and vendor data is automatically pulled from your other modules, such as the IT Risk Assessment and Vendor Management module, populating BIA dependency lists. This is not only an efficient way to use work that had already been built out, but also allows you to check that work from an entirely different perspective.
Ultimately, you’re going to put in a lot of effort to build out a Business Impact Analysis that properly appeases your regulators. You might as well make sure you are using that information to benefit your overall Business Continuity Plan, help you mitigate additional risk to your organization, and make better business decisions. In the end, that is the real reason those BIA requirements are there in the first place.


.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
