Have you recently been through an audit or exam and received a recommendation to develop data flow diagrams (DFDs)? Have you reviewed your cybersecurity practices and noticed that mapping data flows is emphasized in frameworks like NIST’s Cybersecurity Framework (CSF) 2.0? The framework's asset management category specifically calls for organizations to document how data moves within their systems and to external parties. If this has left you wondering where to start or why DFDs matter, you’re not alone.
Understanding how data flows through your network — where it’s stored, how it’s transmitted, and who has access to it — is a critical step in managing risk and strengthening security.

What Is a Data Flow Diagram?
The FFIEC "Architecture, Infrastructure, and Operations" IT booklet (2021) defines a data flow diagram as “a graphical representation of the flow of data internally through the entity's network(s), business units, products, and software, and to third parties, as applicable. Data flow diagrams and network diagrams may include similar information (e.g., critical hardware) but have different purposes. Data flow diagrams show how the entity’s data flows between critical hardware on the network, not just where a piece of hardware resides.”
Although creating DFDs is a baseline cybersecurity maturity control — meaning that all financial institutions are expected to have them — many organizations struggle to develop them or even understand their importance.
A DFD may include:
- Storage locations of data (data at rest) and data movement between systems (data in transit), especially for sensitive data
- Data sharing between applications
- References to network diagrams for details on internal and external connectivity
- Specific operational or business processes and any single points of failure
- Data flow within the entity (e.g., operational or business process interactions and interdependencies) and between the entity and third-party service providers
A DFD should:
- Supplement an organization's understanding of how information flows within and between network segments — and across the perimeter to external parties
- Identify data sets and subsets shared between systems
- Identify applications that share data
- Highlight the classification of transmitted data
The FFIEC "Architecture, Infrastructure, and Operations" booklet also discusses network diagrams, which are visual representations of a network's architecture, showing how devices, systems, and connections are arranged within it. Many organizations mistakenly assume that a network diagram serves the same purpose as a DFD, but the two are distinct. While they may share some overlapping details, a DFD is an entirely separate requirement that serves a different but equally important purpose.
In smaller or less complex IT environments, data flow and network diagrams may be combined. In larger or more complex IT environments, organizations typically maintain multiple DFDs and network diagrams structured in various ways (e.g., by line of business, geographic location, network segment, or business function).
Why Data Flow Diagrams Are Important
Mapping data flows isn’t just a best practice — it’s a recognized requirement in leading cybersecurity frameworks. NIST’s CSF 2.0 highlights the importance of understanding how data moves within and beyond your network to manage risks effectively. But why is this so critical?
Financial institutions and other organizations are more reliant than ever on third-party vendors for daily operations. As part of vendor management, it’s crucial to understand how data is stored, transmitted, and processed outside your network. More information is being handled externally than within your own infrastructure. The big question is: Do you know where your data will go once it leaves your network?
If you're interested in exploring this further, consider enrolling in the SBS Institute’s Certified Banking Vendor Manager course to learn more about the critical aspects of vendor data management.
How to Create a Data Flow Diagram
The main challenge organizations face with DFDs is knowing where to start. Since we’ve defined what a DFD entails, the next step is identifying which vendors store, transmit, and process your data outside your network.

One of the most effective ways to create a DFD is to look at your critical business processes, which you should have identified in your business impact analysis. It’s important to step through the flow of each process and pinpoint where customer information is sent.
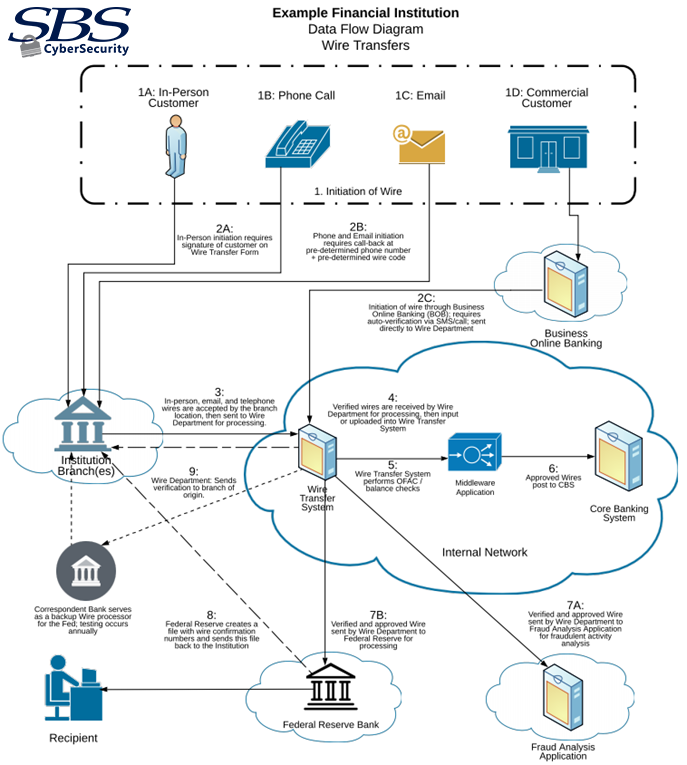
Let’s take wire transfers as an example. There are multiple ways to initiate a wire transfer:
- In person
- Over the phone
- Via email
- Through an online banking platform
Where does the customer information go after the request is initiated? Consider the following:
- Through which entity or vendor does it pass?
- Where does it ultimately end up?
This line of questioning will lead you to the DFD answers you need.
Start by creating DFDs that depict:
- The actors involved at different steps in a critical business process (including people, technology, and third parties)
- Whether those actors store, transmit, or process customer information
- The points at which customer information enters or exits the network perimeter
- How information flows between each actor throughout the business process
Following this model, your DFDs will:
- Help you understand where your customer information flows across the perimeter to external parties
- Identify which external parties receive customer information
- Identify applications, systems, and vendors that share customer information
You may notice that network segment flows aren’t included here. While you can certainly add them, they are typically covered in network diagrams.
The Path to Clearer Data Flow Diagrams
Data flow diagrams don’t have to be complicated. In fact, a well-crafted DFD can give your organization a much clearer understanding of how your data moves once it leaves your network and who handles it along the way. Be consistent in your approach, and ensure it’s grounded in solid risk assessment data from your business impact analysis and IT risk assessment.
Data Flow Diagram Example
![]()
Get Expert Help with Data Flow Diagrams


.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)