Proofpoint’s 2024 statistics on phishing revealed that 76% of cyberattacks in 2023 stemmed from spear-phishing campaigns targeting specific members within organizations. In that same year, consumers reported almost two million unique email-based threats. It only takes one email and one employee’s click to give a hacker access to your network and expose your organization’s sensitive data.
Leveraging Open-Source Information for Effective Phishing
One of SBS CyberSecurity’s network security engineers conducted a social engineering assessment during a comprehensive audit for a client. This assessment involved simple open-source information gathering, utilizing popular platforms like LinkedIn and Facebook to collect personal details about the client’s vice president of human resources. This information was then used to craft a deceptively authentic phishing campaign targeting internal employees, simply requesting them to verify their details in the purportedly “updated employee directory.”
The engineer sent 23 phishing emails to employees. Remarkably, eight employees clicked on the embedded “Here” link, which directed them to a landing page controlled by SBS CyberSecurity and captured their IP information for further investigation.
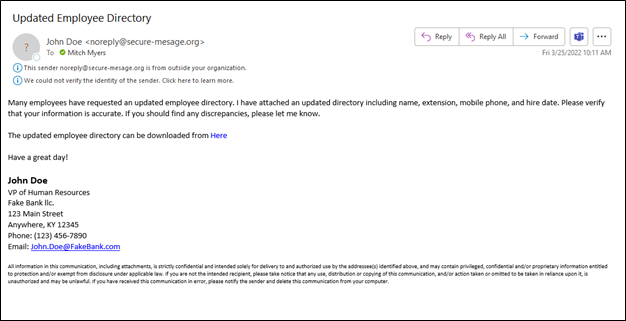
Sample phishing email used in this assessment.
The landing page was populated with the client’s logo, and the page title was changed to resemble a bank-owned site. Here, the login page entices employees to provide credentials to view the newly “updated employee directory.” Three of the eight original employees who clicked the link within the email provided their credentials on the landing page. Usually, frustrated by not reaching the promised directory, they would attempt different credentials, mistakenly thinking they had erred initially, thereby providing the engineer with multiple sets of credentials for each affected employee.
This example underscores the critical need for vigilant email handling and robust phishing awareness training within organizations to prevent such breaches.
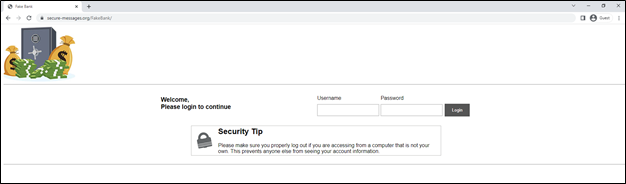
Sample landing page used in this assessment.
Gaining Internal Network Access Through Phishing
As part of the full audit conducted by the SBS engineer, VPN portals were pinpointed as a critical component of the client’s external network exposure. Leveraging the credentials obtained from the phishing campaign, the engineer attempted to log in to the VPN portal.
Sample VPN portal used in this assessment.
Expecting a multifactor authentication (MFA) prompt, the engineer was surprised to find that the employee whose credentials were being used had not set up MFA yet. This oversight allowed the engineer to set up MFA on his own device, effectively bypassing what should have been a critical security layer.
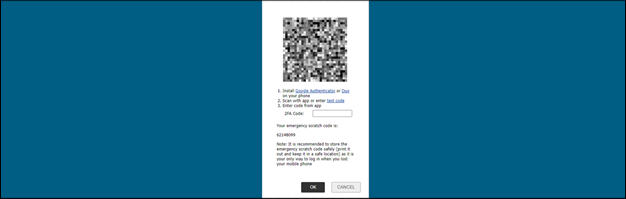
Sample multifactor setup used in this assessment.
After setting up MFA, the engineer was prompted to download the VPN client to his device, which he configured with the VPN server’s information. The successful launch of the VPN client gave the engineer a VPN portal into the client’s internal network.
Once inside, the engineer utilized network scanning tools such as Net Scanner, NMAP, and EyeWitness to explore and assess the access level within the subnet he had landed on. This phase of the assessment aimed to determine the breadth of network access that could be achieved through a single phishing-compromised account.
Sample VPN portal used in this assessment.
Implementing Controls to Mitigate Phishing Threats
Effective controls are essential in combating phishing attacks. Start by ensuring your mail server is configured to reject spoofed emails automatically. It’s crucial to adjust your spam filters and quarantine settings to prevent potentially harmful phishing emails from reaching your employees. Additionally, having MFA enabled for all external login pages and ensuring that it is configured correctly can prevent a hacker from gaining access to your internal network using credentials that may have been stolen from a phishing email.
Depending on the app or service, there are ways to enforce user enrollment. Cloud services like Microsoft Azure, Microsoft 365, and Amazon Web Services have MFA enforcement policies that can be configured to require MFA setup before the user’s next login or within 14 days of policy enforcement. Teaching users of MFA to always deny anything they didn’t initiate directly is also a necessary piece of the puzzle. The SBS team has seen credential thefts when the client had MFA installed just because the user thought they were getting logged out automatically, so they approved the MFA when an attacker initiated the action with stolen credentials.
Phishing Tips for Employees

Phishing emails feature common indicators that everyone can look for to prevent falling for scams, revealing personal information, or becoming susceptible to malware. Typical signs of a phishing attempt include:
- Generic greetings
- Spelling errors
- Language that evokes a sense of urgency in the victim
- Requests to send personal or financial information
- Shortened URLs that hide an untrustworthy website
- Unexpected attachments
Follow these best practices when reviewing an email:
- Check the sender’s email address for misspellings, and if it is someone you know, reach out to them via another contact method to confirm the message’s legitimacy.
- Hover over any links to ensure the linked text matches the URL before clicking.
- Be mindful not to click an “unsubscribe” button, as this may be another misleading link.
- Avoid clicking unknown links or attachments.
- If you are still unsure of the email, report it to the information security team at your organization (or via the “report spam” button in your email inbox), and delete the message.

If you suspect you have been a victim of a phishing attack in a work setting, immediately follow your company’s phishing policy and report the incident to the appropriate contacts.
Key components of phishing awareness within any organization are testing and internal communication. Send out test phishing emails regularly to keep employees vigilant and make sure they are familiar with the latest tactics. These tests should be followed by feedback sessions to discuss successful phishing detection and improvement opportunities. A proactive approach and open lines of communication between the IT security team and employees are important to prevent these types of attacks and build a culture of awareness around phishing.
Responding to Phishing Incidents
A proactive cybersecurity culture requires that all employees are trained on the phishing policy and know the exact steps to take when they spot a phishing email or accidentally click on one. Management should provide positive reinforcement when phishing tests are caught and reported to encourage vigilance and develop an environment where employees feel comfortable reporting incidents quickly.
A comprehensive phishing incident response plan is essential to taking immediate, effective action if an attack occurs. This plan should include clear protocols for protection, detection, and response. Protect against phishing by training employees to recognize threats, verifying email sources, testing suspicious content, and requiring extra identity checks for secure access. For detection, set up systems to flag suspicious emails and encourage employees to report anything unusual. In the response phase, isolate affected emails, monitor for signs of compromise, and update security settings to prevent similar attacks in the future. Regularly reviewing and testing your incident response plan helps ensure everyone is prepared to handle potential threats effectively.
A Stronger Network Begins with Prepared Employees
Layered security measures are recommended as best practices in protecting your network. Employee education through training is a significant first step in giving your personnel the right tools when dealing with a potential phishing email. Products such as KnowBe4 allow organizations to simulate phishing attacks, offer targeted training, and assess employee proficiency in recognizing and responding to phishing attempts, thereby strengthening your organizational cybersecurity posture. For more detailed strategies for responding effectively to security incidents, including phishing, consider exploring this comprehensive guide on building an incident response playbook.
![]()
Phishing Awareness




.png?width=400&name=SBSIWebinarsBundles_WebMenu%20(1).png)
